How do forensic experts investigate a hard drive?
Find out how forensic experts analyze a hard disk to recover digital evidence, recover deleted files and reconstruct activity history.
Discover practical guides, technical analyses, and proven tools to prevent intrusions, protect your connections, and strengthen your infrastructure. Modern solutions to safeguard your data and systems: encryption, authentication, network protection. Designed for curious individuals and businesses striving for excellence.
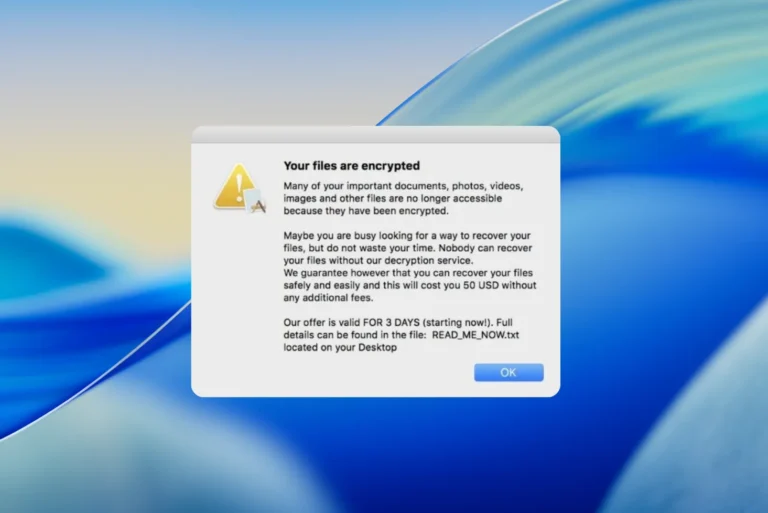
macOS is no longer spared: ransomware is increasingly targeting Apple users in 2025. Find out more.

Tails OS is a secure, portable operating system designed to protect your anonymity, bypass censorship and erase all traces after use.
Find out how forensic experts analyze a hard disk to recover digital evidence, recover deleted files and reconstruct activity history.
Temporarily disable Windows Defender in just a few clicks. Follow our guide to pause Windows’ built-in antivirus.
Discover WPA3, the new Wi-Fi security protocol designed to replace WPA2. What are its improvements? Why is it more secure? How do you activate it? All the answers here.
A new computer scam is spreading: crooks are faking breakdowns to get victims to call fake technical support and pay for non-existent repairs. Find out how to protect yourself.
Find out how to verify file integrity in Windows using MD5 and SHA-256 fingerprinting. Protect yourself against corrupted or falsified files.
A free alternative challenges everything you know about cybersecurity… and antivirus companies would rather you ignore it.
Don’t take any risks. Follow our recommendations for securing your camera, detecting intruders and guaranteeing your online privacy.
Protect your accounts with 2FA! This article explains the TOTP and HOTP methods for secure, convenient one-time passwords.
A zero-day vulnerability affects all versions of Windows, allowing attackers to steal NTLM credentials simply by opening a malicious file.
The U.S. government is facing criticism from Elon Musk over the state of its IT infrastructure, deemed inefficient and outdated.
In the age of the all-connected, where our daily interactions are mediated by screens, digital identity has become an inescapable
Practical Guide to Disinfect Your Web Browser with ZHPCleaner. Follow our steps to remove unwanted software.
Install a completely free ad blocker to protect you from malicious sites and ads on the Internet.
Don’t be left in the dark! Explore the various categories of malware and arm yourself with the knowledge to secure your system.