The best free antivirus programs for home users in July 2025
Discover our selection of the best free and paid antivirus products, tested and compared to help you choose the best protection.
Discover practical guides, technical analyses, and proven tools to prevent intrusions, protect your connections, and strengthen your infrastructure. Modern solutions to safeguard your data and systems: encryption, authentication, network protection. Designed for curious individuals and businesses striving for excellence.
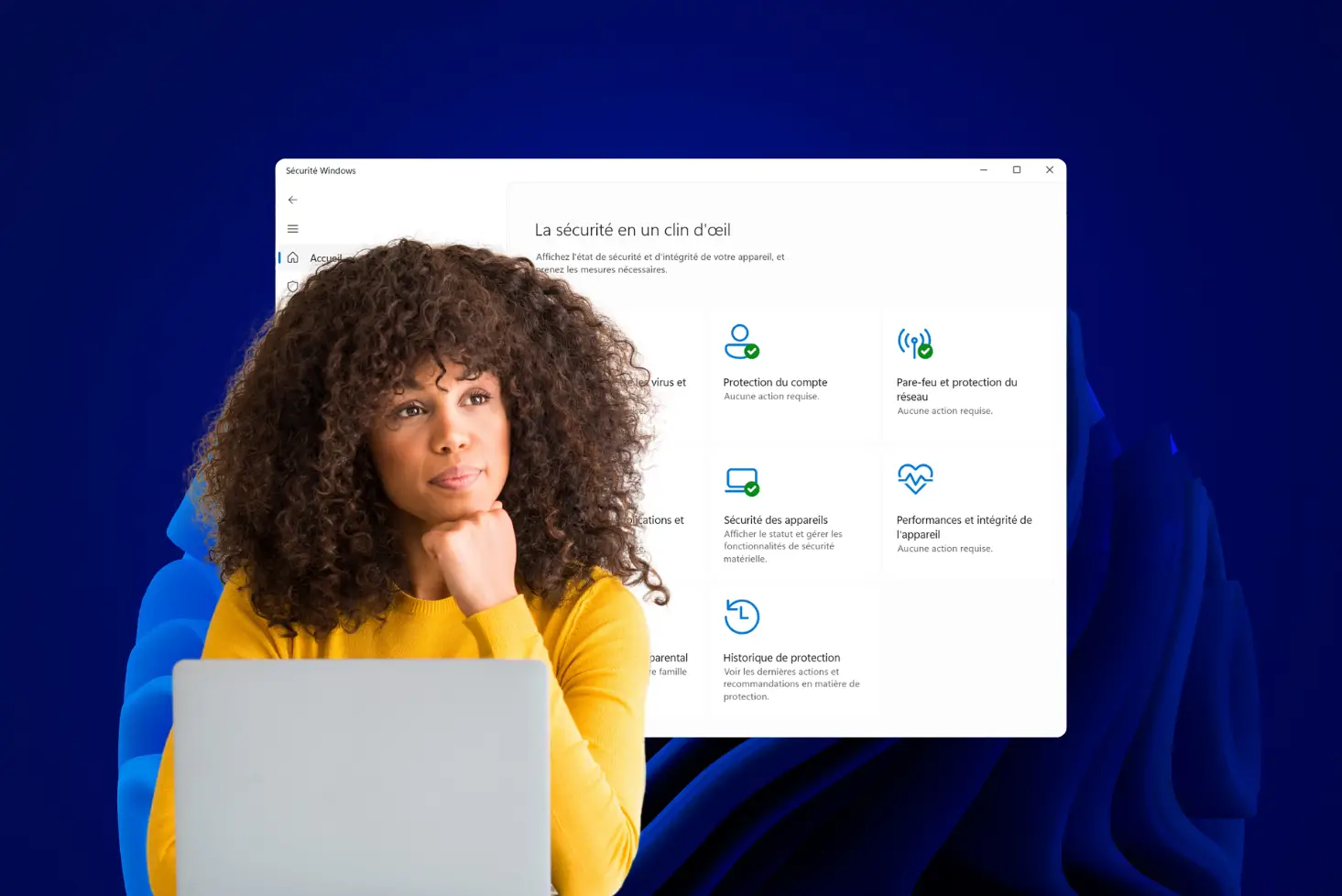
Wondering whether Microsoft Defender is a reliable antivirus? In-depth analysis of its protection capabilities for your PC in 2025.

Discover how tampered USB-C cables become powerful espionage tools. Protect your devices and data with our practical tips.
Discover our selection of the best free and paid antivirus products, tested and compared to help you choose the best protection.
Wondering whether Microsoft Defender is a reliable antivirus? In-depth analysis of its protection capabilities for your PC in 2025.
Discover how tampered USB-C cables become powerful espionage tools. Protect your devices and data with our practical tips.
Discover WPA3, the new Wi-Fi security protocol designed to replace WPA2. What are its improvements? Why is it more secure? How do you activate it? All the answers here.
Discover the best VPNs for PCs in 2025: anonymous browsing, advanced encryption and unlimited access to your favorite content. Secure your connection now!
Find out how to secure your online data at no cost! Immerse yourself in these practical tips and start surfing with peace of mind.
A free alternative challenges everything you know about cybersecurity… and antivirus companies would rather you ignore it.
Access Wi-Fi passwords stored in Windows! Find out how to easily view your network security keys via your Wi-Fi connection settings.
Don’t take any risks. Follow our recommendations for securing your camera, detecting intruders and guaranteeing your online privacy.
Protect your accounts with 2FA! This article explains the TOTP and HOTP methods for secure, convenient one-time passwords.
A zero-day vulnerability affects all versions of Windows, allowing attackers to steal NTLM credentials simply by opening a malicious file.
In the age of the all-connected, where our daily interactions are mediated by screens, digital identity has become an inescapable
Install a completely free ad blocker to protect you from malicious sites and ads on the Internet.
Protect your WordPress site against cyberthreats. Learn best practices to strengthen security with our tips.
Don’t be left in the dark! Explore the various categories of malware and arm yourself with the knowledge to secure your system.