Think your password is enough to secure your online accounts? Think again. Cyber-attacks are on the increase, and hackers are becoming ever more ingenious. Two-factor authentication (2FA) is a formidable weapon in the fight against these threats. Find out in this article how multi-factor authentication works and improves cybersecurity.
What is two-factor authentication (2FA) ?
- Alarming statistics on password security
- 2FA: Pirates don’t have the last word
- How does two-factor authentication (2FA) work?
Alarming statistics on password security
Password security is a major concern, and the figures speak for themselves. According to a recent study, 81% of data breaches are due to weak or compromised passwords. This finding underlines an alarming reality: many people continue to use risky practices that expose their sensitive information to cyber-attacks.
Among the most frequently compromised passwords are classics such as 123456, password, admin and qwerty. Despite expert warnings, 25% of users still admit to using easy-to-guess passwords. Worse still, 39% of Internet users reuse the same passwords on several accounts, enabling hackers to quickly access multiple services once a single password has been compromised.
Cybercriminals also use sophisticated tools such as brute force or dictionary attacks to test millions of combinations in a matter of seconds. In the face of these threats, the average lifespan of a weak password is virtually nil when targeted.
2FA: Pirates don’t have the last word
Unlike simple password verification, 2FA relies on double validation: what you know(your password) and what you have (such as a temporary code sent to your phone or generated by an application). This second layer of security renders stolen or guessed passwords useless. For example, if a hacker manages to gain access to your password via a data leak or brute force attack, he’ll find himself blocked when a 2FA code is required.
The figures bear this out: with 2FA enabled, the risk of intrusion drops drastically, as hackers now have to overcome an additional hurdle that they cannot easily bypass.
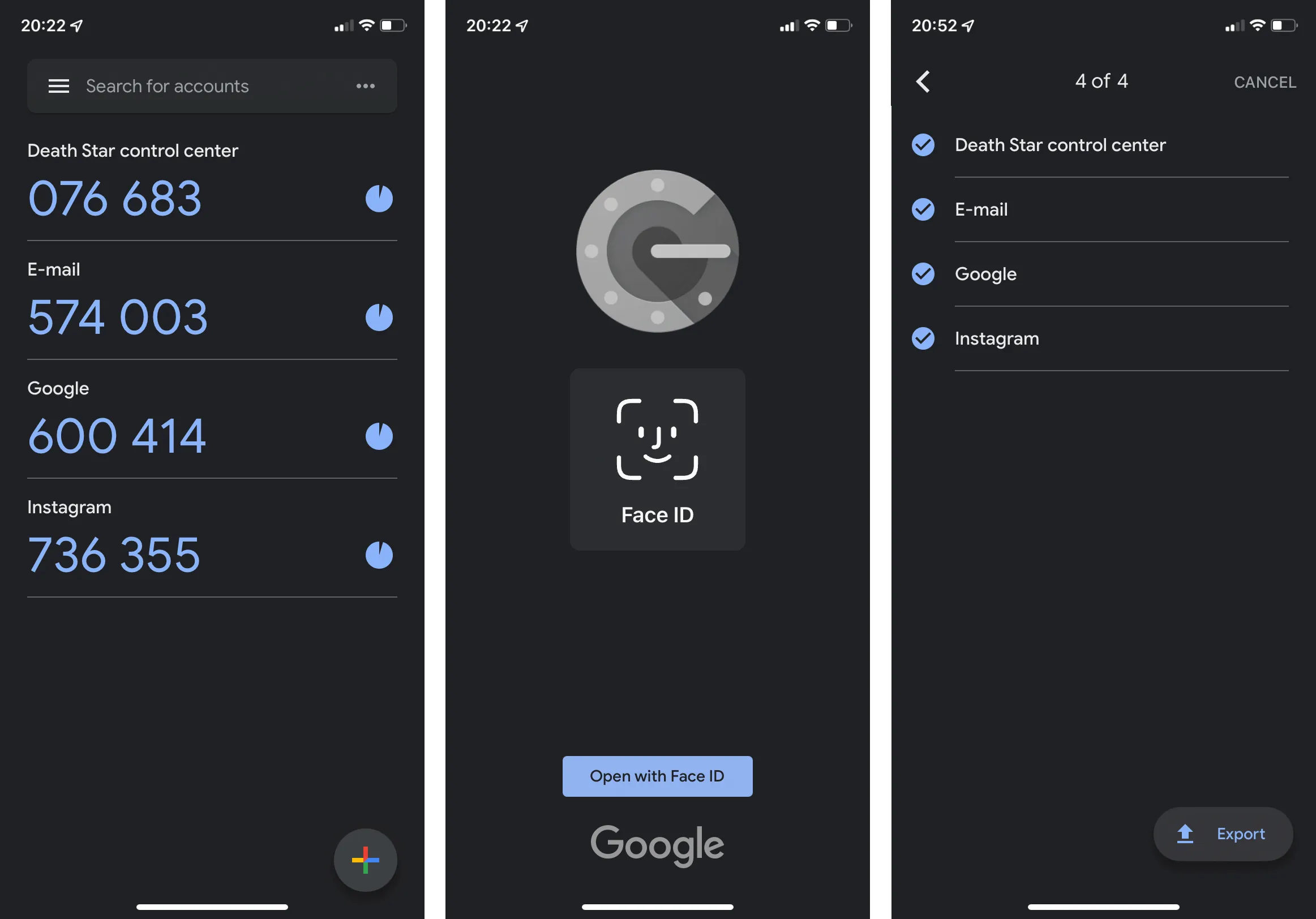
Applications such as Google Authenticator, Microsoft Authenticator and FreeOTP are free solutions for generating unique temporary codes.
By adopting 2FA, you don’t give hackers the chance to go through with their attack. This technology allows you to maintain control over your accounts, even if your password is compromised. After all, in the battle for online security, it’s better to be prepared than unarmed.
How does two-factor authentication (2FA) work?
Two-factor authentication (2FA) is based on the requirement for two distinct proofs ofdigital identity. These proofs usually combine something you know (a password) and something you possess (a code or device). Even if a hacker manages to obtain your password, he won’t be able to access your account without the second factor.
There are several methods for generating this second factor, the most common being based on the TOTP and HOTP algorithms, which work with physical applications and devices.
TOTP: Time-Based One-Time Password
TOTP is a time-based method of generating temporary codes.

- Time synchronization: The authentication server and your device (smartphone, security key) use a common clock to generate a unique code.
- Code calculation: An algorithm takes as input a shared secret key (generated during configuration) and the current time, then produces a temporary code.
- Expiration: This code is valid for a limited time, usually between 30 and 60 seconds. Once expired, a new code is generated.
And so on, indefinitely.
HOTP: HMAC-Based One-Time Password
HOTP is a counter-based method of generating one-time passwords.
- Incremental counter: HOTP uses a counter that increments with each code generation.
- Secret key: As with TOTP, a secret key is shared between the server and the user’s device.
- Code calculation: An algorithm combines the secret key and the counter to produce a unique password.
Codes are not time-dependent, which can be useful in contexts where time synchronization is difficult, but requires rigorous counter management to avoid desynchronization.
HOTP is often used in hardware devices such as RSA tokens or YubiKeys to provide unique passwords with no time dependency.