Although ransomware encrypts your files to make them inaccessible, all is not necessarily lost. Some ransomware families have been broken or abandoned by their creators, allowing cybersecurity experts to offer free decryption tools. In this guide, you’ll find a complete and up-to-date list of the official decryptors available in 2026 and the ransomware supported. Real hope if your data is being held hostage.
Decrypt ransomware: the complete list of free tools to recover your files in 2026
- What is ransomware?
- Victim of ransomware? Here’s what not to do
- Identify ransomware with Crypto Sheriff (No More Ransom)
- What tools can I use to decrypt ransomware for free?
- Emsisoft: a vast library of free decryptors
- Avast / AVG: targeted tools for individual download
- Bitdefender: decryptors from international surveys
- Trend Micro: one tool for many ransomwares
What is ransomware?
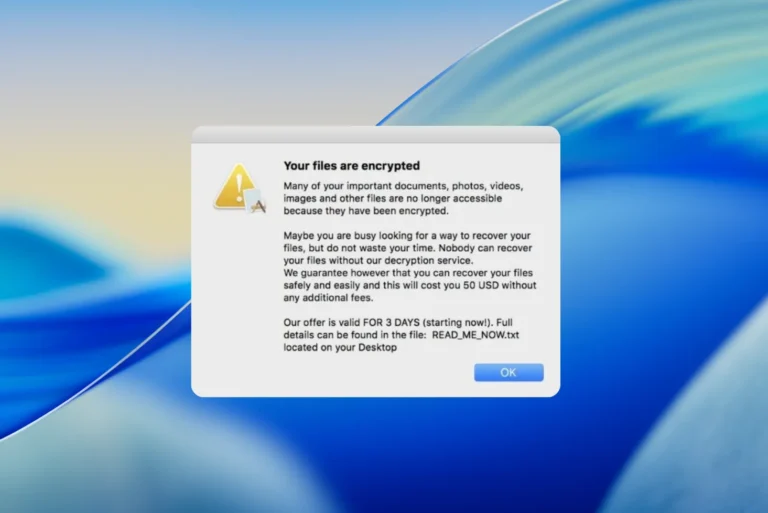
Ransomware is malicious software designed to encrypt a user’s files or block access to their system, then demand a ransom in exchange for a decryption key. Victims often discover an explicit note indicating the amount to be paid (often in cryptocurrency) and the steps to be taken to hopefully recover their data.
You can see your files, but not open them. Without the private key held by the attackers, the content is unreadable.
Ransomware is not a homogeneous group. There are several families, each with its own mechanisms and objectives:
- Crypto-ransomware: these are the most widespread. They encrypt user files (documents, images, databases, etc.) but leave the system functional. Examples: STOP Djvu, CryptoLocker, TeslaCrypt.
- Locker-ransomware: completely blocks access to the system, displaying a lock screen (often with a false authority message). Files are not encrypted, but the computer is unusable. Examples: WinLocker, Police Virus.
- RaaS (Ransomware-as-a-Service): this model commercializes ransomware. Cybercriminals create a tool that they “rent” to other groups, in exchange for a commission on ransom payments. Examples: REvil, LockBit, Hive.
Each family uses different extensions, ransom messages and attack vectors (booby-trapped attachments, exploits, RDP attacks, etc.).
But not all ransomware is infallible. Free tools exist to unlock certain types of infection, when a group has made a technical error, has been dismantled, or its keys have been leaked. Companies such as Kaspersky, Bitdefender and Emsisoft are working with law enforcement agencies to offer decryptors capable of restoring files without paying a cent.
Discover also the best software to protect you from ransomware.
Victim of ransomware? Here’s what not to do
Faced with a frozen screen or unreadable files, panic can quickly get the better of you. But certain mistakes can make the situation worse, and make decryption impossible. Here are the reflexes to avoid:
- Never delete your encrypted files. Even if they seem unusable, they are still essential for eventual recovery. Some decryption tools require the original files to work.
- Don’t pay the ransom without exploring all the alternatives. There’s no guarantee that you’ll receive a key, and every payment feeds criminal groups. Many ransomware programs can now be decrypted free of charge.
- Don’t use unverified tools found on forums or suspicious sites. Some so-called decryptors are actually malware in disguise, or can irreversibly damage your files.
Before taking any action, correctly identify the strain (see below), then use only the recognized tools listed in this guide.
Identify ransomware with Crypto Sheriff (No More Ransom)
Before considering decryption, it’s important to know which ransomware you’re dealing with. File extensions, ransom notes, infection styles… Variants abound, sometimes with misleading names. To avoid randomly testing a tool (and potentially aggravating the situation), it’s best to use Crypto Sheriff, the identification service developed by the No More Ransom project.
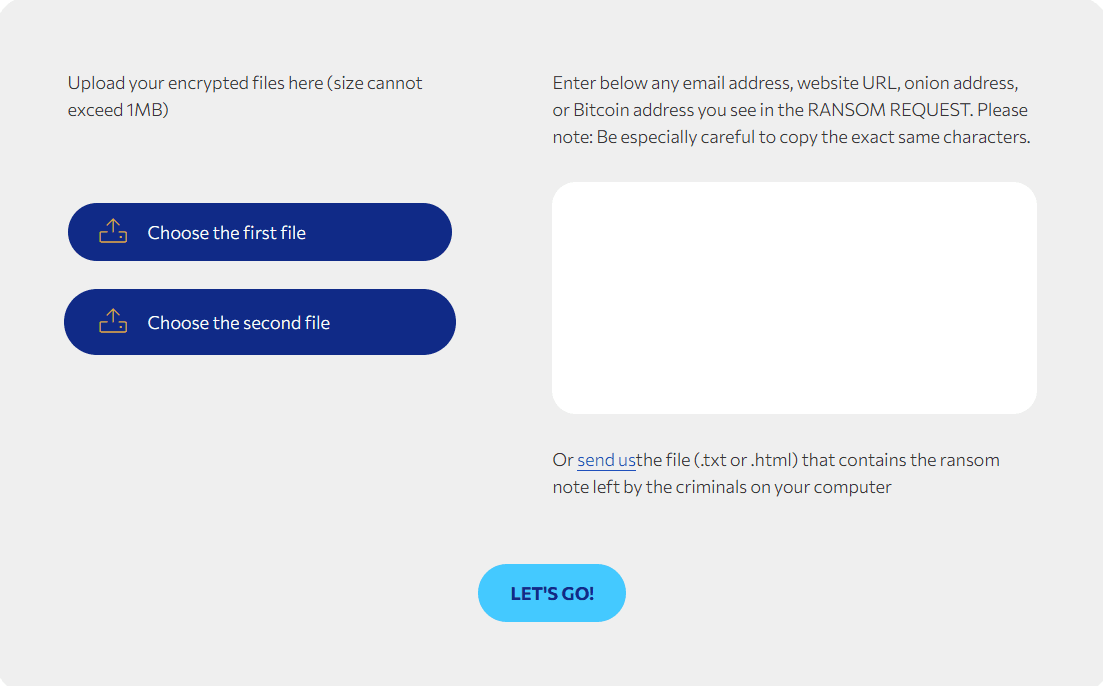
You upload an encrypted file, ideally a non-sensitive document, and if possible add the contents of the ransom note left on your machine ( .txt or .html file, or contents displayed at startup). Based on these two elements, Crypto Sheriff analyzes the file’s structure and known signatures, and tells you which strain it corresponds to, with a bonus link to the decryption tool (if one exists).
STOP Djvu, Dharma, Phobos, LockBit, GandCrab, all the big names. And if no solution is available at the moment, it’s best to know before wasting time or further corrupting your data.
What tools can I use to decrypt ransomware for free?
Each ransomware family uses different encryption. Some have been broken, others have had their keys leaked or seized by law enforcement agencies. As a result, free decryption tools exist, but they are specific to each variant.
Below, we have compiled a list of the most reliable tools. All links lead to official, tested and verified sources.
Kaspersky: the No Ransom project against ransomware
For several years now, security vendor Kaspersky has been offering an initiative called “No Ransom”, dedicated to the fight against ransomware. This project provides the public with a collection of free tools capable of decrypting files held hostage by certain ransomware programs. The aim is clear: to enable victims to recover their data without paying the ransom, while raising awareness of good security practices.
The tools on offer cover a wide range of ransomware families, some of the most widespread or destructive of recent years. Here are some of the variants currently supported:
- Rakhni and its hybrid variants (Agent.iih, AutoIt, Rotor, Bitman, etc.)
- Shade(a.k.a. Troldesh), whose decryption keys have been published by the creators themselves
- CoinVault and Bitcryptor thanks to joint operation with Dutch police
- TeslaCrypt (up to version 4)
- Cryakl, Jaff, Wildfire, Xorist, Rector, Pletor, Yatron, Dharma, Maze, Egregor, Fonix, Conti…
Each tool is independently Windows-compatible, and comes with an explanatory sheet specifying supported variants and instructions for use. These utilities have been developed on the basis of legally recovered keys, technical flaws in ransomware or data supplied by the authorities during the dismantling of cybercriminal groups.
You can find the full list of tools and download links on the official project page.
Emsisoft: a vast library of free decryptors
A recognized specialist in the fight against malware, Emsisoft offers one of the most comprehensive libraries offree ransomware decryption tools. These utilities are developed in-house or in collaboration with law enforcement agencies, using keys recovered from investigations, public leaks, or flaws discovered in the encryption algorithms used by cybercriminals.
The Emsisoft decryptor database covers over 100 ransomware families. Among the best-known are :
- STOP Djvu: the world’s most widespread ransomware. Emsisoft’s decryptor can restore files if the variant uses an offline key (not specific to the victim). Typical extensions are
.djvu,.gero,.rumba, etc. - Amnesia and Amnesia2: two very active strains for 2017-2019.
- Aurora: a fearsome ransomware distributed as a service (RaaS).
- BigBobRoss: targeted mainly North American users.
- Other families such as Apocalypse, Cry9, Cry128, Xorist, GandCrab, Jigsaw, BTCWare, Globe, etc., are also supported.
Some decryptors, like the one for STOP Djvu, can only work in very specific cases: for example, if the ransomware has used an offline key (shared between victims), and not a unique online key generated by the attackers’ server. In this case, the tool displays a message indicating whether the files are decryptable or not. It is therefore essential to test the tool without modifying the files.
The complete library is available on this official page.
Avast / AVG: targeted tools for individual download
Avast, which also owns the AVG brand, offers a wide selection offree decryption tools for individuals and businesses infected by ransomware. Unlike other vendors who centralize everything in a single interface, each Avast tool is dedicated to a specific family of ransomware, enabling light, fast and targeted execution.
The library covers some thirty different ransomware variants, including several of the most active in recent years. Supported variants include :
- GandCrab (up to version 5.2), for which the keys were released in 2019 after the dismantling of the group
- AES_NI, known for its attacks on companies and public institutions
- CrySiS / Dharma, one of the most widely distributed ransomwares via RDP
- HiddenTear, used in numerous open source clones distributed on GitHub
- And many others: Bart, Alcatraz Locker, Apocalypse, BigBobRoss, Jigsaw, TeslaCrypt, Stampado, SZFLocker, XData, etc.
Access the full list of tools on the official Avast website.
Bitdefender: decryptors from international surveys
Bitdefender stands out in the fight against ransomware through its active collaboration with Europol, the FBI, Interpol and other government agencies. This cooperation has made it possible to develop and publish free decryptors for some of the most formidable ransomware of the last decade.
Unlike other vendors who rely on technical flaws or attacker errors, Bitdefender often works with keys recovered during legal takedowns. These operations sometimes result in the publication of decryptors capable of restoring the files of thousands of victims worldwide.
Among the ransomware supported by Bitdefender’s tools are :
- REvil / Sodinokibi: decryptor published after seizure of infrastructure and keys in 2021.
- DarkSide: famous for crippling the Colonial Pipeline in the USA.
- GandCrab: all versions up to 5.2, after publication of a universal key.
- Avaddon: decipherer made available after the group’s voluntary shutdown.
- But also: MegaCortex, LockerGoga, RanHassan, MortalKombat, WannaRen, MaMoCrypt, Paradise, Ouroboros, and many others.
Each tool is self-contained and includes an interface with built-in instructions. The procedure is generally straightforward: select a folder, launch the scan, wait for decryption to finish.
All tools are accessible from the official Bitdefender Center.
Trend Micro: one tool for many ransomwares
Unlike other vendors, who offer a separate tool for each ransomware application, Trend Micro focuses on simplicity, with a single tool called “Ransomware File Decryptor”. This all-in-one utility automatically detects the ransomware family responsible for the encryption and launches the decryption process if a solution is available.
One of this tool’s major assets is its compatibility with several ransomware families, including some older or poorly coded ones. In particular, it supports the following variants:
CryptXXX, TeslaCrypt, Jigsaw, Petya/NotPetya, WannaCry, Nemucod, XORBAT, Crysis, BadBlock, Stampado, and other families occasionally supported depending on version.
The interface, though simple, features a “batch” mode, useful for folders containing a large number of encrypted files. You can also run a targeted scan on a specific directory, to avoid scanning the entire disk. The program automatically indicates whether the ransomware is recognized and whether decryption is possible.
Thetool is available free of charge on the official website.