Surfing the Deep Web intrigues as much as it worries. Yet much of this hidden Internet is perfectly legitimate, used to bypass censorship, consult sensitive information or preserve privacy. Today, the Tor browser is the best-known gateway to this parallel network, where anonymity is the order of the day. In this article, you’ll find out how Tor works, how to use it correctly, and above all, how to limit the risks when accessing .onion sites on the Dark Web in 2026.
Deep Web: how to use Tor to access the Dark Web in 2026
- Tor: What is the Deep Web and the Dark Web?
- Installing and configuring Tor on Windows
- How to access the Dark Web and best practices
- The best tools to strengthen your anonymity on the Dark Web in 2026.
Tor: What is the Deep Web and the Dark Web?
The term Deep Web refers to all Internet content that is not indexed by traditional search engines. This doesn’t necessarily mean illegal or dangerous data: private messaging, academic databases, corporate extranets, bank forms… these are all part of the Deep Web, because these pages require authentication or are deliberately not accessible to the public.
The Dark Web, on the other hand, is a small part of the Deep Web accessible only via anonymous networks like Tor. It hosts .onion sites, invisible without a specific browser. Some of these sites are legitimate (independent journalism, help forums, secure messaging), others much more controversial (black markets, extremist forums, illegal content). Anonymity is strengthened, but so are the risks.
Tor is the main tool for exploring this hidden Web. It encrypts traffic and masks the user’s IP address, making browsing difficult to trace. But while Tor protects your technical identity, it doesn’t protect you from everything. Caution is essential, because the Dark Web is not a safe space by default, and even less so a space without consequences.
⚠️ Warning: If you’re a sensitive person, be aware that the Dark Web can expose you to shocking, illegal or disturbing content. Some pages display violent images, extreme language or criminal activities. Navigating the Tor network requires caution, hindsight and an awareness of the risks involved.
Installing and configuring Tor on Windows
The Tor browser is available free of charge on the official website for all major operating systems: Windows, macOS, Linux and Android. We recommend you always download the latest version from this site to avoid counterfeits or compromised versions (common on the Deep Web).
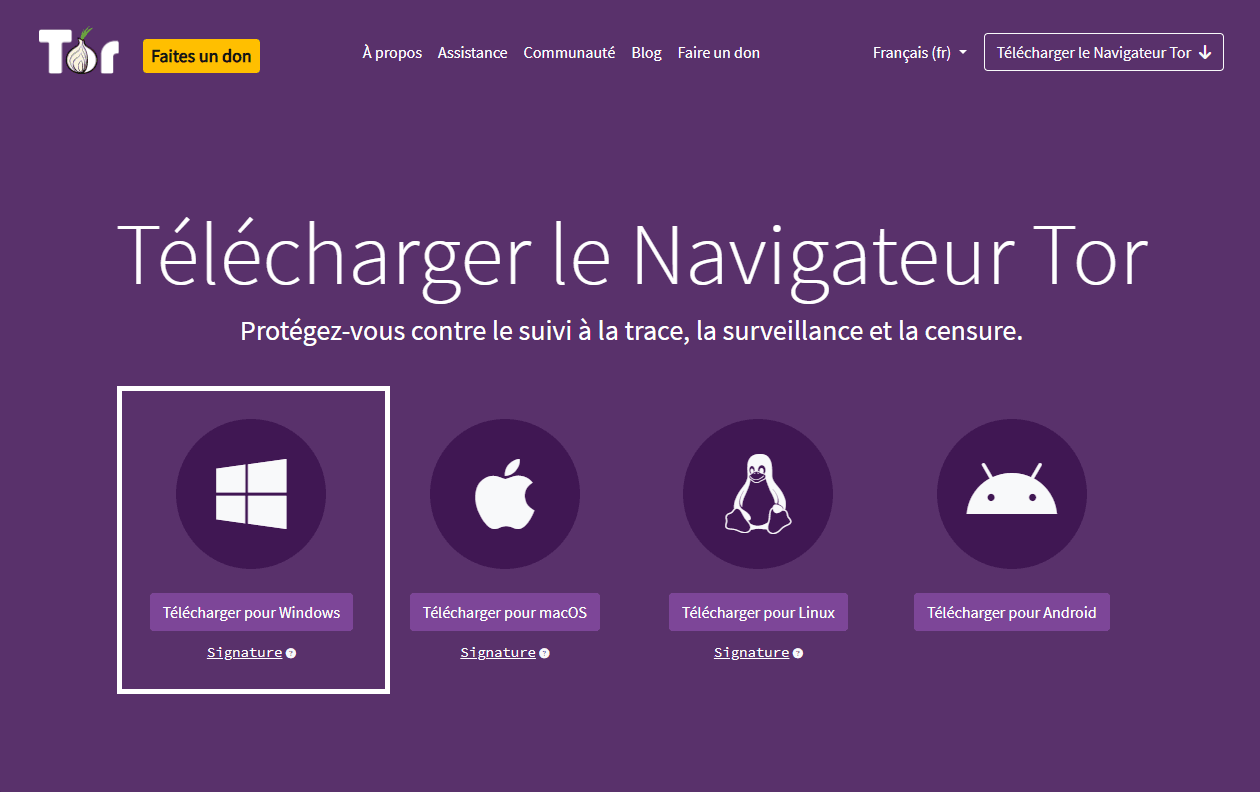
Once downloaded and installed, it’s essential to carry out an initial minimum configuration before browsing the Deep Web.
How to connect to the Tor network for the first time
On first launch, the Tor Browser asks you to connect to its network. By default, connection is automatic: just click on “Connect”.
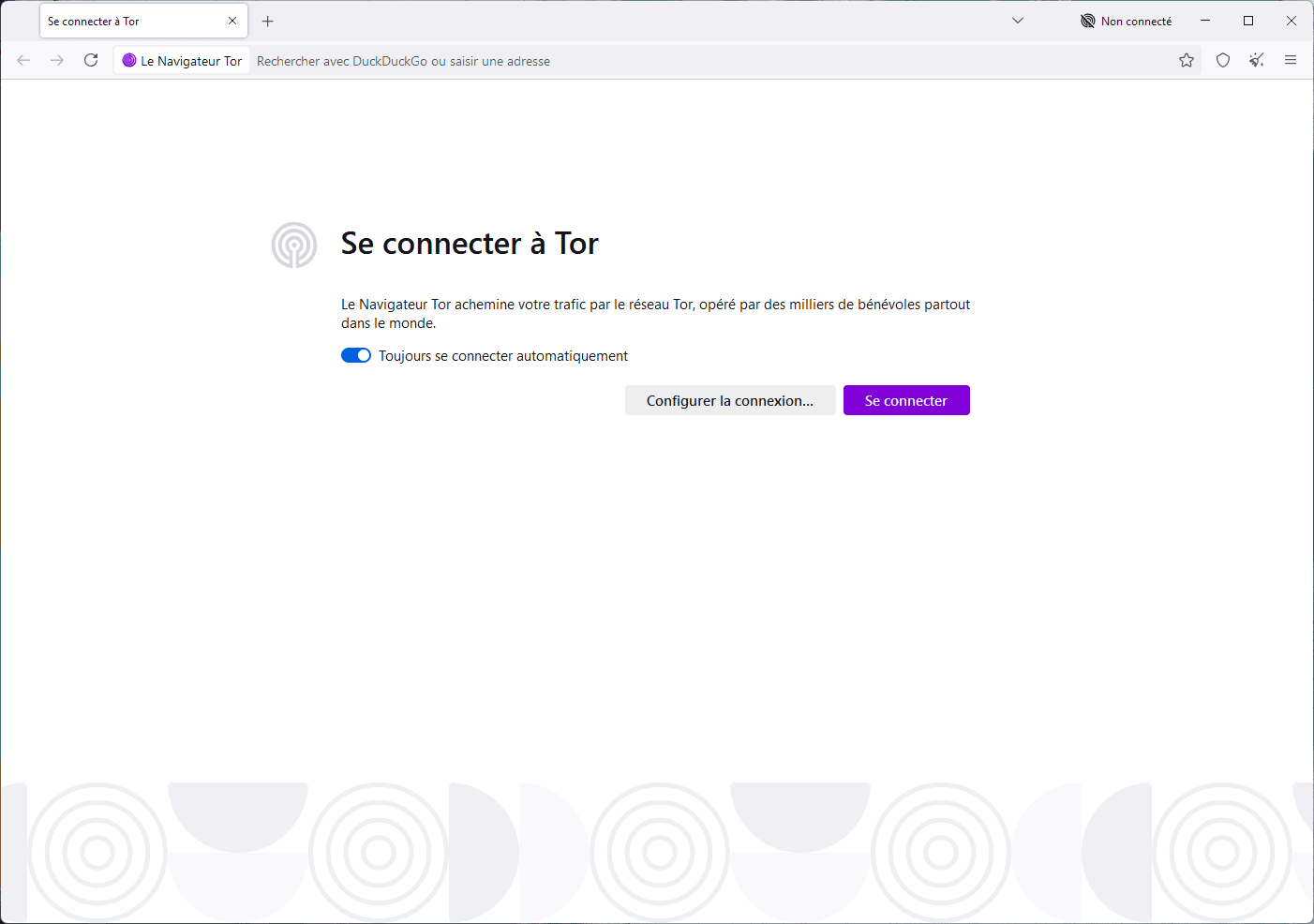
Check the “Always connect automatically” option to avoid having to validate this step every time you start up. This guarantees a fast connection for every session.
In the event of network restrictions (censored country, corporate firewall, etc.), a “Configure connection…” button lets you manually adjust bridge or proxy parameters.
Tor: how to strengthen your security before surfing the Deep Web
Once logged in, you are strongly advised to adjust your browser’s security level, accessible via the shield icon in the top right-hand corner of the interface.
- Click on the shield icon, then on Settings.
- Choose the “Safer” mode, which disables :
- JavaScript on non-HTTPS sites
- some custom fonts
- HTML5 and WebGL media (autoplay disabled).
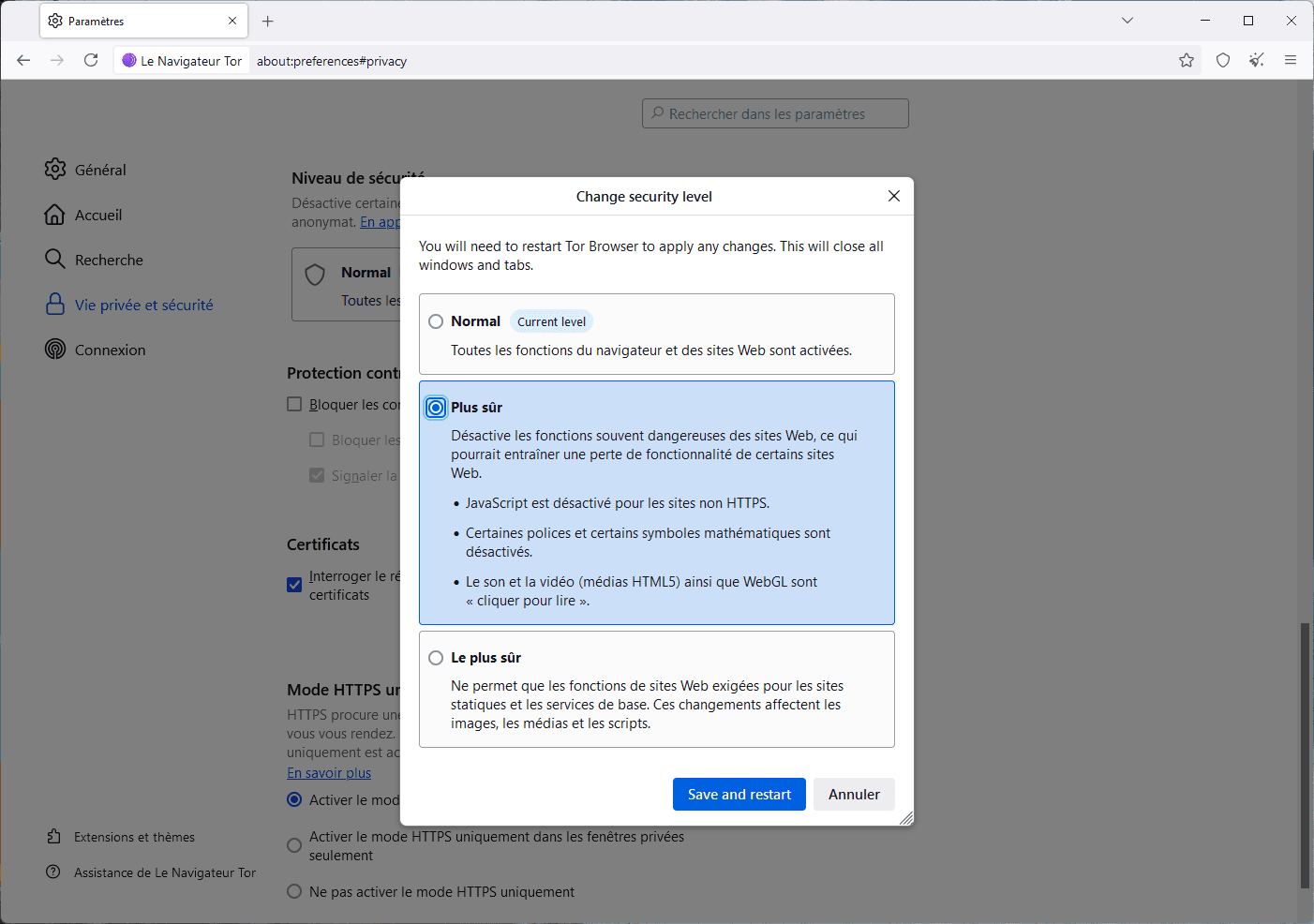
This intermediate level offers enhanced protection without sacrificing site compatibility.
⚠️ Do notinstall any third-party plug-ins or extensions. Unlike conventional browsers, the fewer custom elements there are, the fewer attack vectors there are. Even plug-ins deemed safe elsewhere can compromise your anonymity in this context.
How to access the Dark Web and best practices
Accessing the Dark Web via Tor doesn’t mean venturing in blind. Unlike the classic Web, .onion sites are not indexed by Google. You need to use specialized directories such as Ahmia, The Hidden Wiki or adapted engines such as Torch, Dark Search, Not Evil, Candle or the .onion version of DuckDuckGo, which operates without tracking or history.
Before clicking on a .onion link, it’s essential to check the exact URL. Onion addresses are made up of complex strings that are easy to imitate (ideal for phishing). Never trust a link found on a forum or YouTube video without cross-checking it with a reliable source. Choose pages that are regularly updated or verified by the Tor community (such as the privacytools.io forums or specialized subreddits).
Wikipedia and BBC News have official versions accessible via Tor. These sites allow you to experiment with the .onion network in a secure environment, while respecting good anonymity practices.
The best tools to strengthen your anonymity on the Dark Web in 2026.
Using Tor with simple settings may be enough to explore the Dark Web on an occasional basis. But for those who want to go even further in terms of confidentiality and security, there are specialized tools that can considerably enhance anonymity, notably by avoiding any trace on the system used.
Tails OS: surfing without a trace
Tails OS (The Amnesic Incognito Live System) is a Debian-basedlive operating system designed to run exclusively from a USB stick or DVD. It uses Tor by default for all network traffic and saves nothing to the hard disk: each reboot erases all traces of the previous session. Ideal for activists, journalists or demanding users, Tails offers an isolated, discreet environment, independent of the host system.
Qubes OS and Whonix: for enhanced security
For more advanced use, Qubes OS offers a unique approach to security: each application or usage runs in a separate virtual machine (sandboxing), which drastically reduces the risks in the event of compromise. Combined with Tor-based Whonix, designed to compartmentalize network identity, this provides a high level of protection for experienced or exposed users.
These tools are not mandatory for exploring the Dark Web, but they represent powerful solutions for those who take their anonymity seriously in high-risk contexts (censorship, surveillance, sensitive work, etc.).