When you download a file from the Internet, how can you be sure it’s intact and hasn’t been altered? Accidental corruption or malicious modification can compromise its proper functioning, or even endanger your computer. Fortunately, Windows offers several solutions for verifying file integrity using hashes such as MD5, SHA-1 or SHA-256. This guide explains how to easily compare a file’s hash with that provided by its publisher, using PowerShell or HashCheck.
How to check file integrity (MD5, SHA1, SHA256…) on Windows
- What is a hash mark?
- How to check file integrity with PowerShell?
- Verify a file without technical knowledge (simplified method)
What is a hash mark?
A hash fingerprint is a unique identifier generated by a mathematical function applied to a file. It can be compared to a fingerprint: just as each individual has a unique fingerprint, each file has its own signature that enables it to be identified almost infallibly.
The purpose of hashing is to guarantee that the file has not been altered, either intentionally or accidentally. A simple change of a single character in a file results in a complete modification of its fingerprint, making any alteration immediately detectable.
Case in point:
- An original file could produce this SHA-256 fingerprint:
B73AA55DB50D2AD348F61C6537DA05C0D6DED78A143763454E977BE85B444119- If a single letter or bit is modified, the fingerprint will change completely:
A92BC47F89D31F1B667E8E4D22BC71D5FA23D4AA637845FD8E1A7B2E3D8F093EThis property is essential for verifying that a file has not been altered accidentally or intentionally.
There are various hash algorithms, each of which produces fingerprints of varying length and security:
| Algorithm | Fingerprint length | Security and usage |
|---|---|---|
| SHA-1 | 160-bit | Obsolete, vulnerable to collisions. Not recommended. |
| SHA-224 | 224 bits | More secure variant of SHA-1, but not widely used. |
| SHA-256 | 256 bits | Current security standard, widely used (certificates, blockchain, etc.). |
| SHA-384 | 384-bit | More robust version of SHA-256, used for digital signatures. |
| SHA-512 | 512 bits | Highly secure, but more resource-hungry. |
| SHA-512/224 | 224-bit | Optimized version of SHA-512 for certain applications. |
| SHA-512/256 | 256-bit | Alternative to SHA-256 based on SHA-512. |
| SHA3-224 | 224 bits | SHA-3 algorithm, secure alternative to SHA-2. |
| SHA3-256 | 256-bit | Potential replacement for SHA-256, more resistant to attacks. |
| SHA3-384 | 384-bit | SHA-3 variant for applications requiring enhanced security. |
| SHA3-512 | 512-bit | The most robust SHA-3 version for critical environments. |
Not all hashing algorithms are equal in terms of security. With advances in cryptanalysis, some formats, such as MD5 and SHA-1, are now considered obsolete, as they are vulnerable to collision attacks. This means that an attacker can generate two different files with the same fingerprint and compromise the integrity of the verification process itself…
On the other hand, SHA-256 and SHA-512 offer a high level of security and are today the most widely used standards for guaranteeing the integrity of files and online transactions in the fields of cybersecurity and blockchain.
New algorithms such as SHA-3 and BLAKE2 have been developed to offer a more secure or faster alternative. SHA-3 is based on a different architecture to SHA-2 and offers greater resistance to certain attacks. BLAKE2, on the other hand, is designed to be faster than SHA-3 while retaining an excellent level of security, making it popular for applications requiring fast, secure hashing.
How to check file integrity with PowerShell?
- When a file is downloaded from the Internet, it is essential to ensure that it has not been altered or tampered with. Windows lets you check the integrity and authenticity of a file by calculating its hash fingerprint via PowerShell with the
Get-FileHashcommand.
- Press
Win + X, then select Windows PowerShell.
Alternatively, type powershell in the Windows search bar and press Enter.
In PowerShell, use the following command to calculate the SHA-256 hash fingerprint of a file:
Get-FileHash "C:\Users\Adrien\Downloads\Win11_24H2_French_x64.iso" -Algorithm SHA256
Explanation of order:
Get-FileHash: Command for generating a hash fingerprint."C:\Users\Adrien\Downloads\Win11_24H2_French_x64.iso": Path of file to be scanned (replace with actual path).- –
Algorithm SHA256: Specifies the algorithm used (use the same algorithm as the editor).
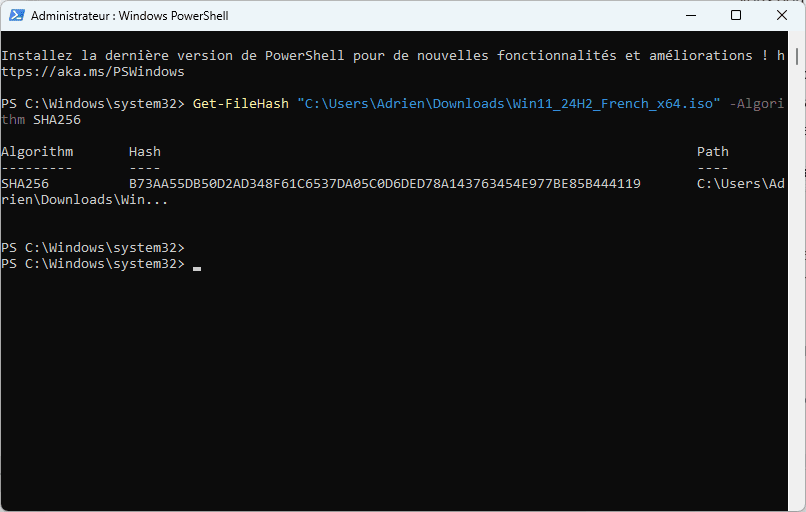
Once the command has been executed, PowerShell will return a hash value, for example :
Algorithm: SHA256
Hash: B73AA55DB50D2AD348F61C6537DA05C0D6DED78A143763454E977BE85B444119
Path : C:UsersAdrienDownloadsWin11_24H2_English_x64.iso
Compare this value with the one provided by the file’s publisher. If the fingerprint displayed corresponds exactly to the official value, the file is intact and authentic.
If you wish to automatically generate and compare the fingerprint with the value provided by the editor, you can also use a variable in PowerShell. This automates the verification process and lets you know immediately whether the file is valid.
$hash_official = "B73AA55DB50D2AD348F61C6537DA05C0D6DED78A143763454E977BE85B444119"
$hash_file = (Get-FileHash "C:\Users\Adrien\Downloads\Win11_24H2_French_x64.iso" -Algorithm SHA256).Hash
if ($hash_file -eq $hash_official) {
Write-Host "✅ The file is authentic and intact." -ForegroundColor Green
} else {
Write-Host "❌ Warning: The file's fingerprint does not match the official value!" -ForegroundColor Red
}This second method eliminates the need for manual comparison and enables immediate detection of any corruption or falsification of the file.
⚠️ If the fingerprints do not match
If the value obtained is different from the official footprint, this may mean that :
- The file was corrupted during download (network problem, corruption).
- It has been deliberately modified (attack attempt or compromised file).
- You have downloaded a file from an unreliable source.
In this case, we recommend that you immediately delete the file and download it again from the official website.
Verify a file without technical knowledge (simplified method)
If you don’t want to use the command line, there are a number of simple, accessible software tools available that allow you to calculate a file’s footprint and compare it with the official value. These tools offer an intuitive graphical interface, suitable for users with no technical skills.
HashCheck (integrated into Windows Explorer)
HashCheck is not installed by default, but you can download it for free from GitHub. Once installed, it integrates directly into the File Properties menu.
Right-click on the file you wish to check.
Click on Properties, then open the Hashes tab (added by HashCheck).
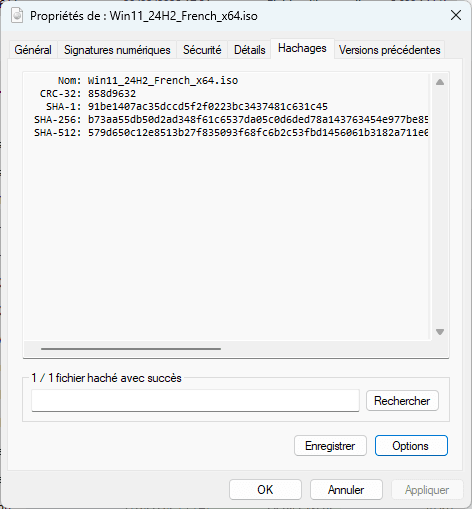
The SHA-256 fingerprint is displayed after being generated.