You click on a program, ready to install it, and Windows asks you for an administrator password that you obviously don’t have. This isn’t a bug, it’s a restriction put in place by your company. You’re stuck, unable to use a tool that could make your life easier. While the intention behind these limitations is laudable, they sometimes hinder more than they protect. Fortunately, there are ways of getting around these restrictions without compromising IT security.
Install Software Without Administrator Rights on Windows
- Why do companies block software installation?
- Windows vulnerability: how to run software without installation or admin rights?
- A complete overhaul of Windows would be required to eliminate this flaw
- In short, how do you get around Windows 11 installation restrictions in the enterprise?
- How to install (without installation) a portable application?
- IT security: How to prevent portable applications from running on Windows?
- AppLocker: How do you block unauthorized software in your company?
Why do companies block software installation?
Companies impose restrictions on software installation primarily for security and compliance reasons. Installing non-validated software can expose the internal network to vulnerabilities such as malware, ransomware and other spyware. Some organizations must comply with strict regulations on data protection and software license management. Allowing software to be installed freely could lead to compliance violations and expose the company to legal and financial risks.
Unauthorized software can also cause technical problems. Some programs may conflict with professional tools already installed, slowing down computer performance or causing instabilities. Poorly optimized or obsolete software can monopolize system resources, affecting the user’s computer and the entire corporate network. By limiting installations to validated software, IT departments can ensure a stable, high-performance working environment.
These restrictions respond to the need for centralized IT management. In a large company, each workstation must be maintained in a uniform way to simplify technical support, updates and cyber security. A system that is too open, where each employee can install his or her own software, complicates maintenance and increases the risk of incidents. By imposing strict controls on installations, companies guarantee better supervision and easier deployment of updates and security patches.
Windows vulnerability: how to run software without installation or admin rights?
Windows, in all its versions, relies on an administrative privilege management model based on UAC (User Account Control). This mechanism is supposed to prevent users without elevated rights from installing or modifying sensitive system files. However, an inherent structural flaw allows portable applications to be run without installation or administrator privileges. Unlike conventional software, which requires registry modification or writing to protected folders, portable applications run directly from a user directory or external media, thus escaping any restrictions imposed by the company or IT department.
This feature exposes a fundamental limitation of Windows security policy. In the enterprise, blocking the installation of software is not enough to restrict its use, as a simple portable executable can provide access to software. Windows does not clearly differentiate between installed and simply executed programs, which leaves the door open to the use of external tools such as browsers, code editors or communication software without prior validation. This flaw is not a bug, but a structural contradiction between the need for system control and the flexibility offered to users.
⚠️ This technique could expose you to severe penalties in your business.
Using a portable application to bypass the installation restrictions imposed by your company may be considered a violation of IT security rules. Many companies have strict policies in place to prevent the execution of unauthorized software in order to prevent the introduction of malware, the leakage of sensitive data or the exploitation of security loopholes. By running a portable program without the explicit agreement of your system administrator, you risk compromising the integrity of the computer network and exposing yourself to disciplinary sanctions ranging from a simple warning to dismissal in the event of a serious infraction. Some secure environments have monitoring systems capable of detecting and blocking the execution of unapproved applications, and any attempt to bypass them may be recorded and analyzed.
A complete overhaul of Windows would be required to eliminate this flaw
A complete restructuring of Windows would be necessary to eliminate this flaw, as the current system is based on a privilege management model that does not sufficiently differentiate between installed and executable software. Today, as long as a program does not attempt to modify protected files or the registry, it can be launched without restriction. This allows portable applications to bypass UAC and corporate restrictions. To truly lock down the execution of unauthorized software, Windows would need to adopt a stricter approach, such as systematic validation of executables, control based on digital signatures, or a more compartmentalized execution environment, similar to that found on mobile operating systems.
However, such an overhaul would pose a number of challenges. Greater control over applications could have a negative impact on the flexibility and user experience that have long been Windows’ strengths. Companies and developers would have to adapt their software to these new constraints, which could lead to incompatibilities and resistance to change. A less radical alternative would be to strengthen monitoring and centralized management of executable applications within business environments, rather than completely overhauling the Windows permissions model.
In short, how do you get around Windows 11 installation restrictions in the enterprise?
If your company blocks the installation of software on Windows 11 via UAC (User Account Control) and administrative restrictions, portable applications are the best alternative. Unlike conventional software, which requires elevated privileges to install itself on the system, a portable application works without registry entries and without modifying system files. Simply download and run it directly from a personal folder, USB stick or external hard drive. This approach enables you to use tools that are essential to your work, such as browsers, advanced text editors or management utilities, without having to ask for IT intervention.
To find reliable portable software, platforms such as PortableApps or even certain standalone versions of open source software are recommended solutions. It’s also possible to run web applications directly from a browser to avoid blocking, or to use authorized virtual machines and sandboxes if your company offers them.
⚠️ Even if these methods don’t technically violate security rules, they may run counter to your company’s internal IT policy.
How to install (without installation) a portable application?
In secure corporate environments, it is common for users not to have the necessary rights to install software. This restriction, imposed to prevent the installation of unauthorized programs, can be circumvented with portable applications. Unlike traditional software, which requires installation with modification of the Windows registry, these programs operate autonomously and can be run directly from a folder or USB stick.
Simulation of a secure environment if you’re not on the premises
To test the execution of portable software in an environment simulating corporate restrictions, simply increase the level of User Account Control (UAC). This modification ensures that any installation attempt requiring administrator rights is immediately flagged. But don’t worry, we won’t need administrator rights.
Downloading and extracting the portable application
Portable applications can be downloaded from an official website (https://portableapps.com/) and run without installation. In the case of LibreOffice Portable, simply download the installation file from the platform or directly from the official software website.
Once the file has been downloaded, this is not a conventional installation, but a simple extraction process. When you launch the executable, an “installation” window appears, asking you to choose a destination folder without administrator rights. The application can be extracted to the computer’s main disk, to the Documents folder or to an external device.
The file extraction process takes a few minutes, during which no system modifications are made. This step allows you to copy all the files needed to run the software, without touching Windows system files.
Once extraction is complete, the software can be run directly. Unlike conventional applications, which require administrator rights for installation and execution, a portable program can be launched by any user, regardless of authorization level.
In our example, LibreOffice Portable is ready for use immediately after extraction. All you have to do is check the option to launch it as soon as the process is complete, or manually open the LibreOfficePortable.exe executable file located in the destination folder. The program then opens normally, with full functionality, without any installation being detected by the system.
While portable software is a great way of getting around installation restrictions, it does have its drawbacks. They run more slowly than software installed directly on the system, due to the lack of optimization and the use of files stored in a temporary directory. This is particularly noticeable when a program is run from a USB stick, where read and write speeds are lower than on an internal disk.
Updates must be performed manually. Unlike an installed version, which updates automatically via Windows Update or a package manager, portable applications require you to download a new version with each update. They do not integrate natively with the operating system: they do not create Start menu entries, and are not associated by default with the file types they can open.
The use of a portable application is a practical solution when it is impossible to install software due to administrative restrictions. This type of program can be run without requiring any special privileges, and is a viable alternative for users who need to bypass technical limitations. However, it should be borne in mind that these programs are generally less powerful than their installed equivalents, and require more manual management for updates.
In a professional context or on a locked workstation, they can be a great help, whether for using a word processor, a browser or even more advanced tools without compromising system security.
⚠️ A cybersecurity expert could exploit these features to bypass certain protections.
For example, a malicious portable program run by a user with restricted privileges could still access personal data and vulnerabilities to spread to other parts of the system…
IT security: How to prevent portable applications from running on Windows?
In an environment where AppLocker and WDAC are not implemented and no execution restrictions are applied to AppData, Temp and Program Files, an experienced attacker can modify a legitimate portable executable using Resource Hacker. This manipulation enables him to inject malicious code without altering the software’s digital signature, making the attack completely undetectable (without behavioral analysis) by conventional security solutions. As soon as an employee runs the modified application, a malicious script runs discreetly in the background, opening up remote access for the attacker to exfiltrate data, capture credentials or even disable Windows protections.
The absence of restrictions on critical directories enables the attacker to propagate the modified executable to multiple machines via open network shares or unmonitored remote access. Once a machine has been compromised, it becomes a pivot point for launching larger-scale attacks by executing commands remotely with PsExec or a simple PowerShell script. This method makes the attack feasible for a simple malicious user with access to an unsecured workstation.
Although this technique is extremely difficult and reserved for offensive security experts, it relies on a structural flaw in Windows: as long as a portable application can be executed freely, no restrictions on software installations really protect the enterprise. The lack of control over executables allows an attacker to maintain a foothold on the network and exploit other vulnerabilities to take full control of the infrastructure.
AppLocker: How do you block unauthorized software in your company?
AppLocker is the most effective solution for preventing the execution of modified or unauthorized software. By defining strict rules, administrators can restrict the execution of applications to software signed by the company or installed in approved directories. This means that an executable placed in AppData, Temp or an unauthorized network share will be blocked before it is even launched (this security rule is very strict and restrictive). But it does neutralize one of the major weaknesses exploited by attackers, making it impossible to run malware in the form of a portable application.
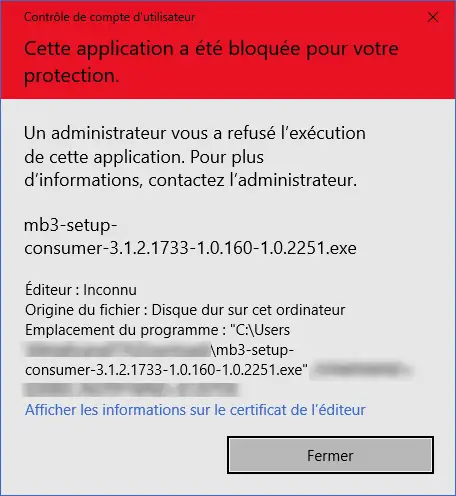
Restricting file execution outside secure directories such as AppData and Program Files is a preventive approach. By applying NTFS restrictions and rules via GPO, administrators can prevent unauthorized execution outside designated locations, and drastically reduce the possibility of a modified executable being exploited. If a user attempts to run a program in an unapproved directory, Windows will refuse execution, thus limiting the risk of stealth attacks.

