macOS has long enjoyed a reputation as a digital fortress. Less targeted, less vulnerable and often perceived as naturally protected, Apple’s system seemed beyond the reach of ransomware. But those days are gone. In 2025, attacks are multiplying, techniques are adapting and Macs are no longer immune. This development is worrying security professionals, especially as it affects a public that is ill-prepared for this new threat landscape.
Ransomware invades macOS and progresses apace
- macOS becomes a target for cyberattacks in 2025
- Record rise in ransomware on the Mac
- A sense of security is no longer enough in 2025
macOS becomes a target for cyberattacks in 2025
For many years, macOS enjoyed a special status in the world of cybersecurity. Thanks to its Unix architecture, native control mechanisms such as Gatekeeper and XProtect, and a more closed ecosystem than Windows, it was perceived as a naturally protected system. This reputation (largely deserved at the time) has contributed to a certain laxity on the part of users: the idea that a Mac doesn’t need antivirus software is still firmly entrenched.
But this apparent tranquility was also due to a volume factor. With a market share historically lower than that of Windows, macOS simply wasn’t of interest to cybercriminals, who gave priority to targeting the most profitable platforms. With fewer machines and lower returns on investment, the economic rationale held back their interest.
This context has changed. Macs are now massively adopted by high-value profiles: content creators, technology startups, the professions, Web3 developers. These are all lucrative targets, often with little awareness of cybersecurity. Malicious groups are adapting, designing macOS-specific attacks and exploiting the blind spots left by users’ overconfidence.
Record rise in ransomware on the Mac
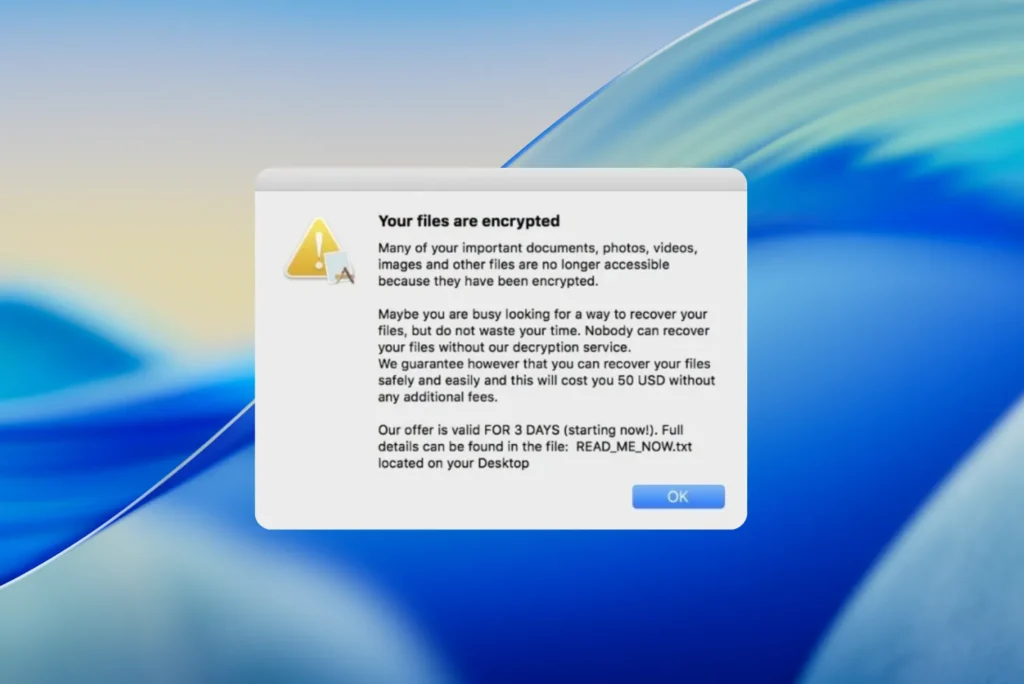
In 2025, ransomware is no longer confined to Windows and Linux environments. According to BlackFog, ransomware attacks have increased by 63% in one year, and macOS is no longer immune to this trend. Cybercriminals are now exploiting specific methods to target Apple computers, taking into account the particularities of the system.
Mechanisms such as Gatekeeper, System Integrity Protection (SIP) or XProtect are now being circumvented by advanced techniques: legitimate code signing, AppleScript scripts, malware embedded in modified apps or distributed outside the App Store. Apple’s default security model is showing its limitations in the face of this new generation of targeted threats.
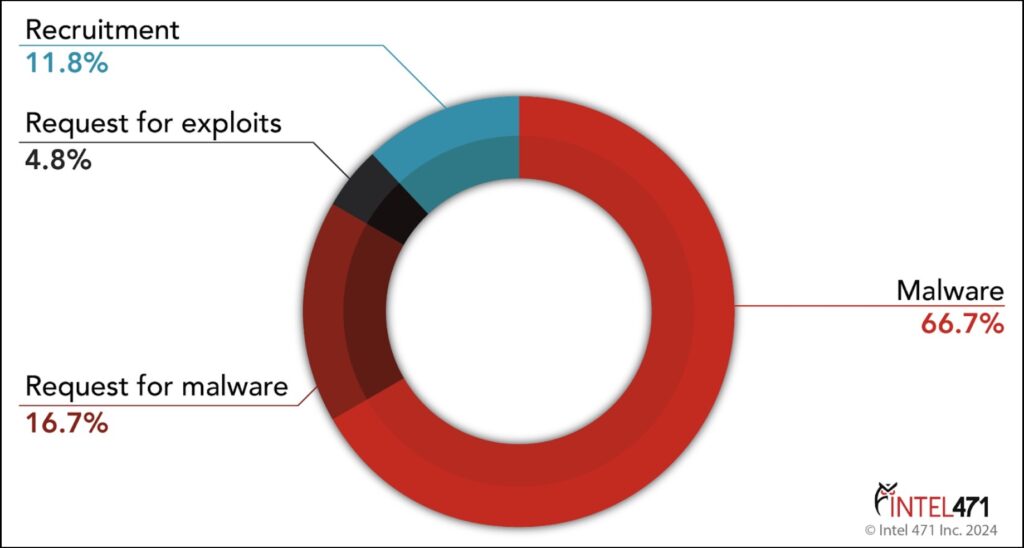
The danger is all the greater in that many Mac users remain convinced that they are protected without any particular effort. This discrepancy between perception and reality plays into the hands of attackers, who find macOS a profitable, under-protected target that is increasingly widespread in professional, creative and technological circles.
A sense of security is no longer enough in 2025
Gone are the days when macOS could boast relative peace of mind in the face of ransomware. The feeling of security still widely held by many Apple users no longer corresponds to the reality on the ground. Cybercriminals are adapting, innovating and actively targeting Mac machines, exploiting their owners’ overconfidence.
Ransomware is no longer a Windows-only problem, but a cross-platform threat capable of hitting all platforms. macOS remains a solid system, but modern attacks know how to bypass its defenses.