Computer fraud is constantly evolving, exploiting the slightest loophole to entrap users. Among them, the fake troubleshooting scam is experiencing a worrying resurgence. Black screens suddenly appear, accompanied by alarming messages urging victims to contact so-called technical support. Behind the scenes, organized cybercriminals take control of devices to extort money and compromise personal data. In the face of this threat, understanding their modus operandi and adopting the right reflexes becomes essential.
The fake tech support scam that can cost you dearly
- The new scam that empties bank accounts
- Anatomy of an attack: from first contact to scam
- Protect yourself from bogus computer repair scams
- Collective intelligence: a weapon against scams
- Report a fake technical support scam
The new scam that empties bank accounts
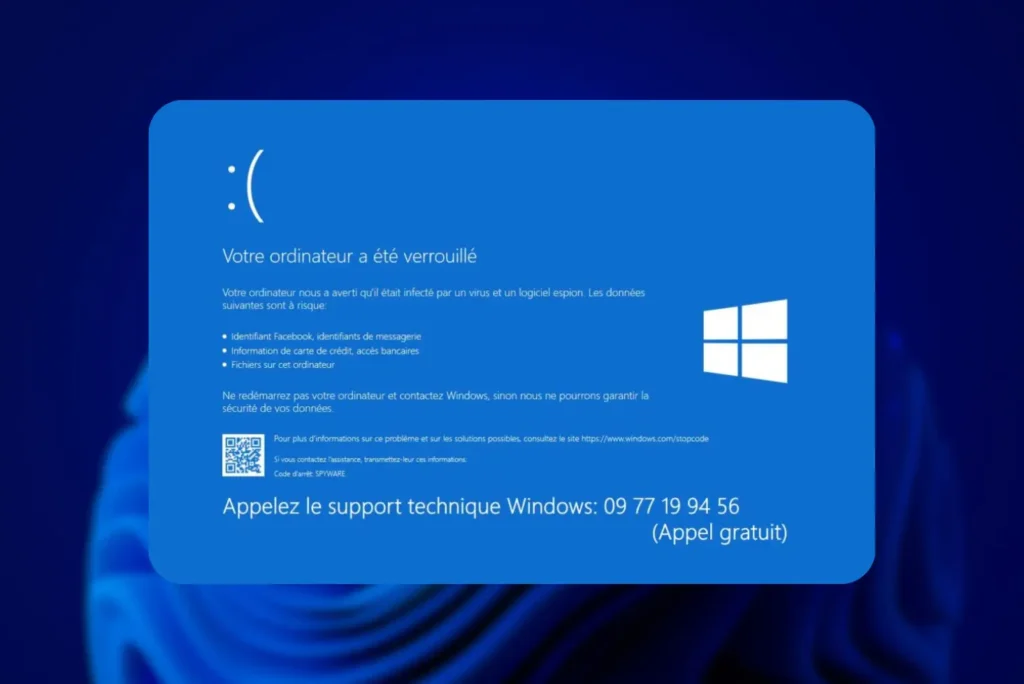
The fake computer troubleshooting scam is based on a simple but highly effective strategy: make the user believe in a critical breakdown, and induce him to contact a fake technical support. The attack begins by infecting the computer with malware accidentally downloaded by the user. This program will then cause the screen to freeze or display an alarmist message indicating a serious problem, such as a critical system error or advanced virus infection.
The fraudulent message then invites the user to call a telephone number presented as an official technical support (Microsoft, Apple, Google, etc.). Once on the line, an alleged technician attempts to remotely take control of the computer using remote IT support software such as AnyDesk or TeamViewer. The ultimate aim is to charge for a fake repair service or install malware to steal sensitive data (bank details, passwords, personal documents).
Anatomy of an attack: from first contact to scam
The fake computer troubleshooting scam follows a well-defined process to deceive users by exploiting their lack of technical knowledge and their instinctive reaction to an emergency situation. Here’s how a typical attack works:
Step 1: Infection and alert message display
It all starts with the intrusion of malware on the victim’s computer. The user may have unknowingly installed it after :
- Having clicked on a fraudulent advertisement claiming to detect a virus on your device.
- Downloading a booby-trapped program disguised as a legitimate update for popular software (browser, video player, antivirus).
- Opening an infected attachment in a phishing e-mail claiming to come from a trusted company.
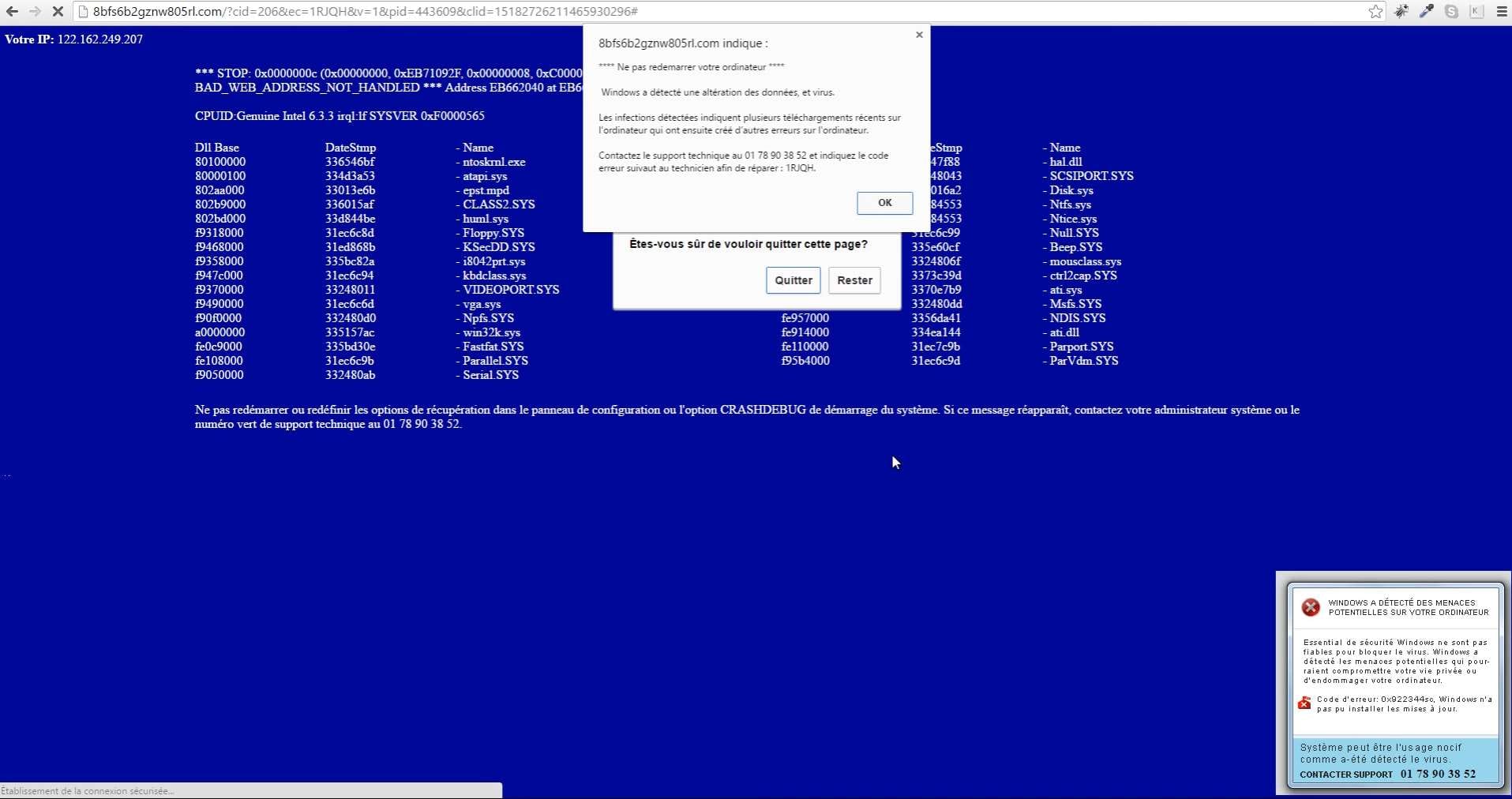
The message is designed to provoke an immediate reaction. It states that the system is seriously infected or that a critical failure is endangering personal data. The tone is alarmist, stressing the need for urgent intervention or irreversible consequences may result. To make the scam more credible, the text displays a logo imitating those of major technology companies such as Microsoft, Apple or Google, and invites the victim to contact technical support via a highlighted telephone number. This staging gives the impression of official assistance and makes the deception particularly effective.
Microsoft, Apple and Google will never display their phone number directly on your computer screen in the form of an alert message or system notification. NEVER!
Step 2: Psychological manipulation and incitement to call
Faced with this worrying alert, the panic-stricken user dials the number displayed, convinced that he must act quickly to prevent the loss of his files or the destruction of his system. As soon as the call is established, it is greeted by a fake technician with a reassuring, professional tone. The technician introduces himself as a technical support agent from a major company, and calmly explains that the situation is critical, but that he can resolve it if certain steps are taken immediately.
At this stage, psychological manipulation is essential. The scammer skilfully plays on fear and urgency to prevent the victim from taking a step back. He uses technical language that is incomprehensible to the untrained user, and insists on the need for immediate intervention. It may also flatter the victim by emphasizing that he or she had the right reflex in calling quickly, in order to reinforce the idea that he or she is in good hands. The aim is to establish a climate of trust sufficient for the victim to agree to follow the instructions he or she will subsequently be given.
Stage 3: Taking control and executing the fraud
Once the victim is confident, the scammer asks him or her to install remote control software under the pretext of carrying out a thorough diagnosis of the problem. Programs such as AnyDesk, TeamViewer or LogMeIn are commonly used, as they allow total access to the computer as if the crook were physically in front of the screen. As soon as installation is complete, the fake technician begins to simulate an intervention. He opens command windows, displays system files presenting them as viruses and pretends to perform scans to give the impression of real expertise.
From this point on, the risk becomes particularly serious. The scammer can operate freely on the victim’s computer, retrieving bank details or installing malware to gain prolonged access to your PC.
Everything is designed to reinforce the idea that the computer is seriously damaged and can only be restored by specialized intervention. At this point, he announces that a solution does exist, but that it requires the installation of antivirus or maintenance software. He explains that this program is essential to repair the computer and prevent the problem from recurring. He also points out that this solution is not free, and costs between 150 and 500 euros.
If the victim hesitates or expresses doubts, the scammer intensifies the pressure. He stresses the risk of permanent data loss and the urgency of immediate action. He may even simulate a total system lock-up to make the threat more credible. Sometimes, he will claim that the computer has already been compromised by hackers and that a theft of personal data is underway, to reinforce the victim’s fear and induce him to accept payment.
Once payment has been made, the scammer often continues to exploit the victim, offering monthly maintenance subscriptions or asking for further payments to supposedly finalize the repair. In some cases, a backdoor is deliberately left on the computer so that the victim can return later for another attempt at fraud.
Protect yourself from bogus computer repair scams
When a fake alert message appears on your screen asking you to call a technical support number, it’s very often a scam. These messages usually come from a malicious website or a fraudulent ad opened in your browser (Google Chrome, Edge, Firefox, etc.). Don’t click on any buttons in the message, and never dial the number displayed.
If your browser seems to be blocked and you can’t close the window normally, here’s the most effective way to regain control of your computer.
How do I close a suspicious process and scan my computer?
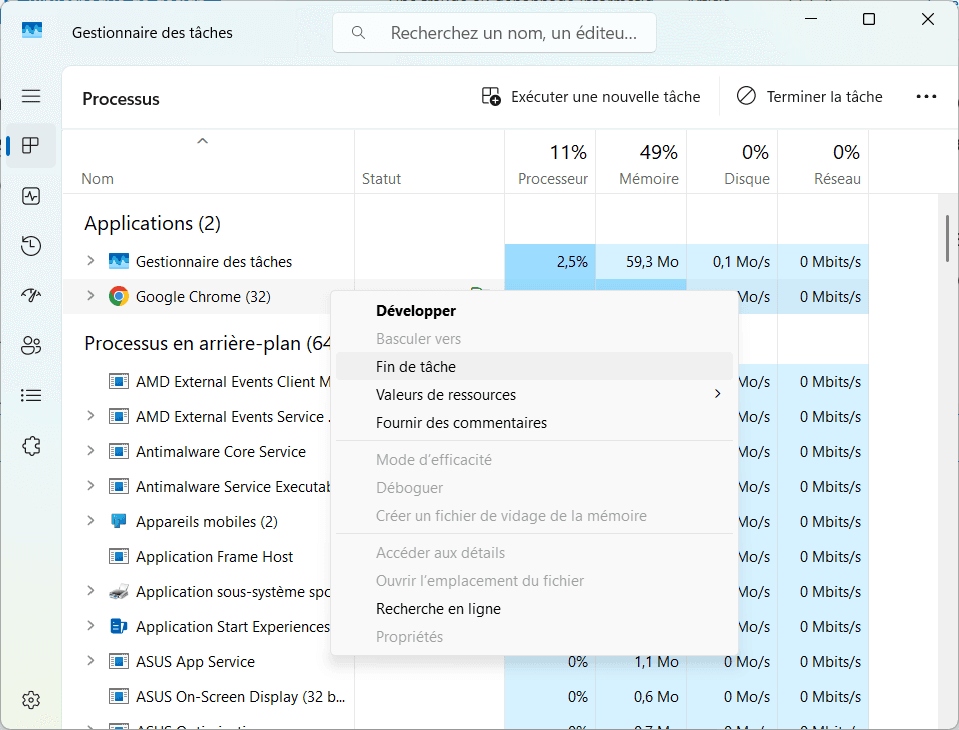
- Open the Task Manager by simultaneously pressing
Ctrl + Shift + Escape. - In the Processes tab, search for your web browser (e.g. Google Chrome, Microsoft Edge, Mozilla Firefox).
- Right-click on the process concerned, then select End task as shown in the image below:
- Once the process is closed, restart your browser without restoring previous tabs, as this could reopen the malicious page.
Run an antivirus scan to remove threats
After closing the browser, we recommend running a powerful antivirus scan to check whether any malware has been installed without your knowledge. You can use ESET’s online scanning tool, a free and reliable solution:
- Go to the site and click on Scan now.
- Download and run the analysis program.
- Follow the instructions to perform a full system scan.
If threats are detected, follow the removal recommendations to secure your device.
Discover our comparison of the best antivirus products to protect your PC.
Collective intelligence: a weapon against scams
Now you’re armed to deal with the fake tech support scam. By understanding the mechanisms of this fraud and adopting the right reflexes, you can avoid falling into the cybercriminals’ trap. Don’t hesitate to share this article with your friends and family, so that they too can protect themselves and recognize these attempted scams.
The more information is circulated, the less impact these scams will have.
When in doubt, it’s always best to contact a real computer troubleshooter. A professional will be able to quickly identify whether there’s a real problem with your computer, or whether it’s the result of fraudulent manipulation. He or she will also be able to guide you in securing your device and preventing your data from being compromised.
Don’t let these crooks thrive on ignorance and fear: get informed, stay vigilant and pass on the information!
Report a fake technical support scam
If you are confronted with a fake technical support scam, it is essential never to call the number displayed or follow any instructions given by the fraudulent message. To avoid being compromised, immediately close your browser using the Task Manager if necessary, then run a full antivirus scan to detect and remove any threats. If remote control software has been installed, uninstall it immediately and change your passwords to secure your accounts.
Once your computer is under control, report the scam to the PHAROS platform via www.internet-signalement.gouv.fr. Describe the incident in detail, mentioning the fraudulent number, the content of the alert message and, if possible, attaching a screenshot. Your report will help the authorities identify and track down these cybercriminal networks.
Find out how to take a screenshot on Windows.
If you have provided your bank details, contact your bank immediately to avoid any fraudulent debit. If you have any questions or require further assistance, contact the Plateforme Info Escroqueries on 0 805 805 817. Don’t keep this information to yourself: spread the word to prevent others from falling into the trap.