They’re everywhere, in your bag, on your desk, and yet you never pay them any attention. USB-C cables, those modern tech essentials, have become the new obsession of hackers. Both discreet and ubiquitous, they’ve become veritable digital Trojan horses, infiltrating your data without you even knowing it.
The hackers’ fearsome new toy: your USB-C cable
- Cybersecurity experts warn: your USB-C charger is a threat
- A booby-trapped USB-C charger is impossible to detect with the naked eye
- Buy a data-blocker: recharge your devices without fear
Cybersecurity experts warn: your USB-C charger is a threat
It’s official: the USB-C cable has conquered the world. Practical and universal, it has become the must-have accessory for recharging our smartphones, laptops and even headphones. But what makes it so successful is also what is increasingly worrying cybersecurity experts.
Yes, you read that right. That little cable we use every day without thinking about it could turn into a real weapon for hackers. A malicious USB-C cable, rigged to infect your devices as soon as you plug it in. A simple recharge and your personal data could be exposed or even stolen.
It’s not science fiction, but a reality. Cybersecurity experts are warning of the emergence of booby-trapped cables, sold online or even distributed in public places.
Each solution brings its own problems
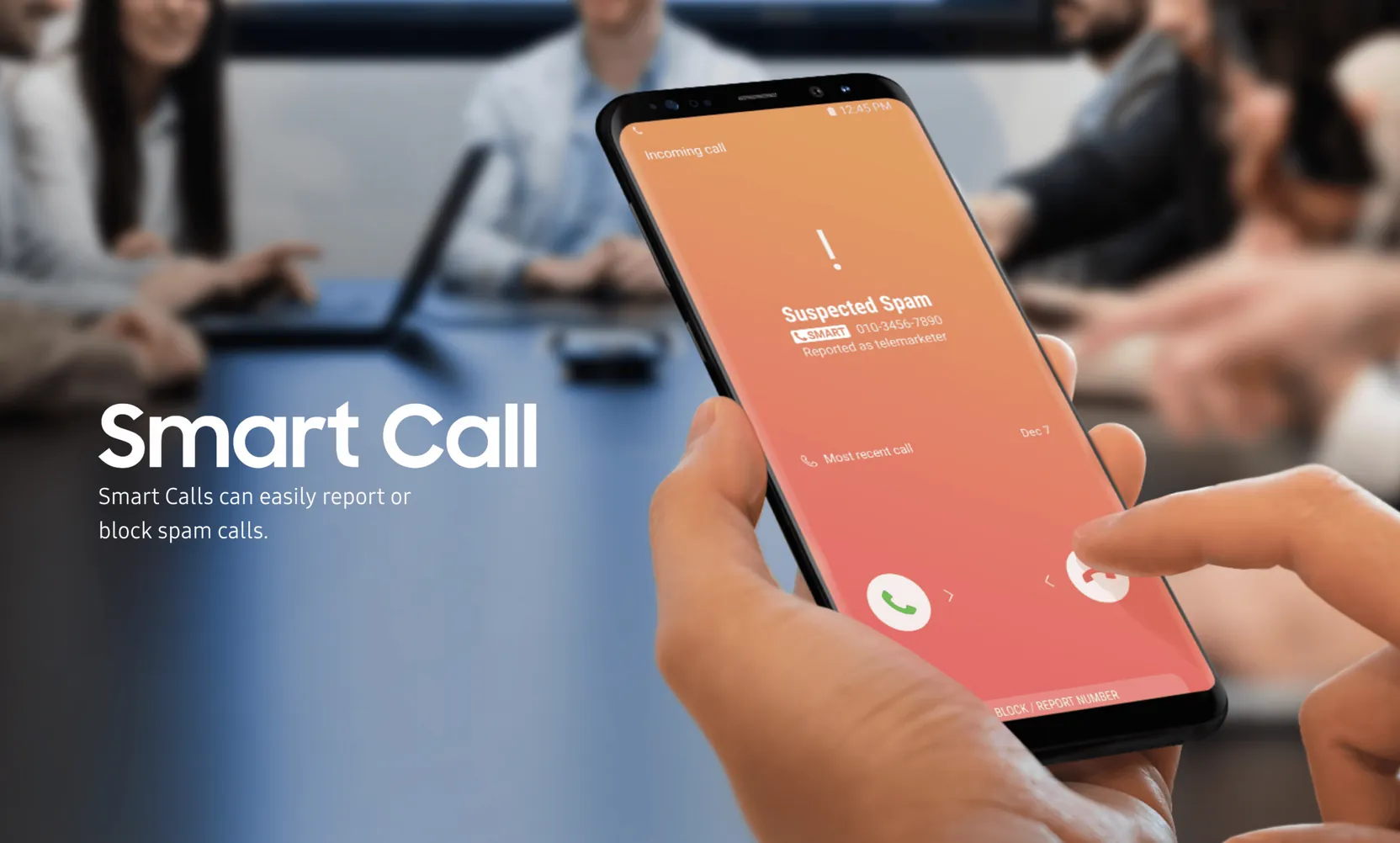
You plug your phone into a USB-C charger in a café or at a public charging point. You think you’re simply recharging your battery. However, behind this harmless charging action, USB-C cables are being tampered with, capable of installing spyware, stealing your data or even taking control of your device.

And it’s no urban legend. These malicious cables, known as booby-trapped cables, resemble in every way those we use every day. Their universality is also what makes them so easy to hijack. Hackers exploit this standardization to infiltrate your devices with the utmost discretion.
A booby-trapped USB-C charger is impossible to detect with the naked eye
It’s a scenario that sounds straight out of a spy movie: a seemingly mundane USB-C charger transformed into a fearsome hacking tool. But the threat is real. And the worst part? These booby-trapped chargers are undetectable to the naked eye.
On the surface, there’s nothing to distinguish a malicious USB-C charger from a genuine model. Same size, same weight, same finish. But inside, hackers insert electronic components capable of infecting your devices as soon as you plug them in. Once connected, the charger can deploy spyware, steal your data or even take control of your device without you noticing.
How to protect yourself from USB-C charger traps?
- Use only cables or chargers from reliable sources. Be wary of free accessories, especially those from unknown brands.
- Avoid plugging your devices into public or shared chargers.
- Invest in a data blocker (see below), a small accessory that prevents any data transfer while you’re charging your device.
Buy a data-blocker: recharge your devices without fear
Today, even something as simple as recharging your phone can expose your personal data. The data-blocker. This little device slips between your cable and your device to block all data transfer, letting only energy pass through. It’s your essential portable shield. Recharge without fear, anywhere, and keep your data in safe hands.

Editor's Verdict :
Compact, pratique et universel, le data-blocker est l’accessoire parfait pour sécuriser vos recharges USB. Son fonctionnement est aussi discret que sa taille, mais son impact sur votre sécurité est immense. À ce prix-là, c’est une précaution qu’il serait dommage de ne pas prendre.
Highlights :
Drawbacks :
Buy at the Best Price on Amazon
A data-blocker cable is an accessory designed to prevent data transfers when charging a device via a USB port. It acts as a filter between your device and the recharging source, allowing only the necessary energy to pass through.
It’s a handy tool for protecting your personal data from potential hackers.