In the age of the all-connected, where our daily interactions are mediated by screens, digital identity has become an inescapable concept. Whether you create an account on a social network, use a banking application or even leave a review on a shopping site, you’re helping to build this digital version of yourself. But do you really know what digital identity is, and how to protect it in a world where our data is worth its weight in gold?
What is digital identity ?
- Definition of digital identity
- The different types of digital identity
- How can I check if my digital identity has been compromised?
- Where do we draw the line between privacy and personal data?
Definition of digital identity
Digital identity, or IDN, is simply the online version of yourself.
It brings together all the information you leave on the Internet: your social networking profiles, your e-mail addresses, your online purchases and even the comments you post on forums.

Simply put, it’s your virtual identity card, made up of visible data (such as your name or photo) and more discreet data (such as your browsing habits). A true reflection of your online activity, digital identity can be both an asset and a risk, depending on how it is managed.
The different types of digital identity
Digital identity encompasses different categories of information, depending on their source, content and author. This data, sometimes disseminated without the user’s knowledge, can affect his or her image or integrity. Understanding these types of digital identity is essential to better control your online presence.
Here are the three main categories of digital identities, according to their origin and nature:
Declarative identity: information about you
Declarative identity includes information voluntarily provided by a person or entity. This data includes :
- Personal information: surname, first name, marital status, etc.
- Official information: addresses, identification numbers, profession.
It’s an identity built on objective data, often used for online registrations or formalities.
Calculated identity or behavioral analysis
Calculated identity is a reconstruction based on the analysis of interactions and data linked to a user. It is used to :
- Create behavioral profiles: buying habits, interests, preferences.
- Personalize the user experience: recommendations, targeted advertising.
This identity is based on algorithms that interpret data left online.
Active identity
Active identity reflects the traces left by online activities, such as :
- Publications on social networks.
- Searches performed or sites visited.
- Interaction with platforms.
This data, sometimes collected on a large scale, is used by companies to develop statistical or commercial analyses. This raises the ethical question of the boundaries between legitimate data collection and respect for privacy.
How can I check if my digital identity has been compromised?
All it takes is one data leak for your personal information to fall into the wrong hands. Your e-mail address, your passwords, even your credit card numbers, can be circulating on the web (and sometimes even on the dark web) without you even knowing it. Fortunately, there are several tools you can use to check whether your digital identity has been compromised:
Check your data with Have I Been Pwned
Have I Been Pwned is one of the most popular tools for finding out if your personal information has been exposed. The site, created by a cybersecurity expert, lists billions of leaked data records.
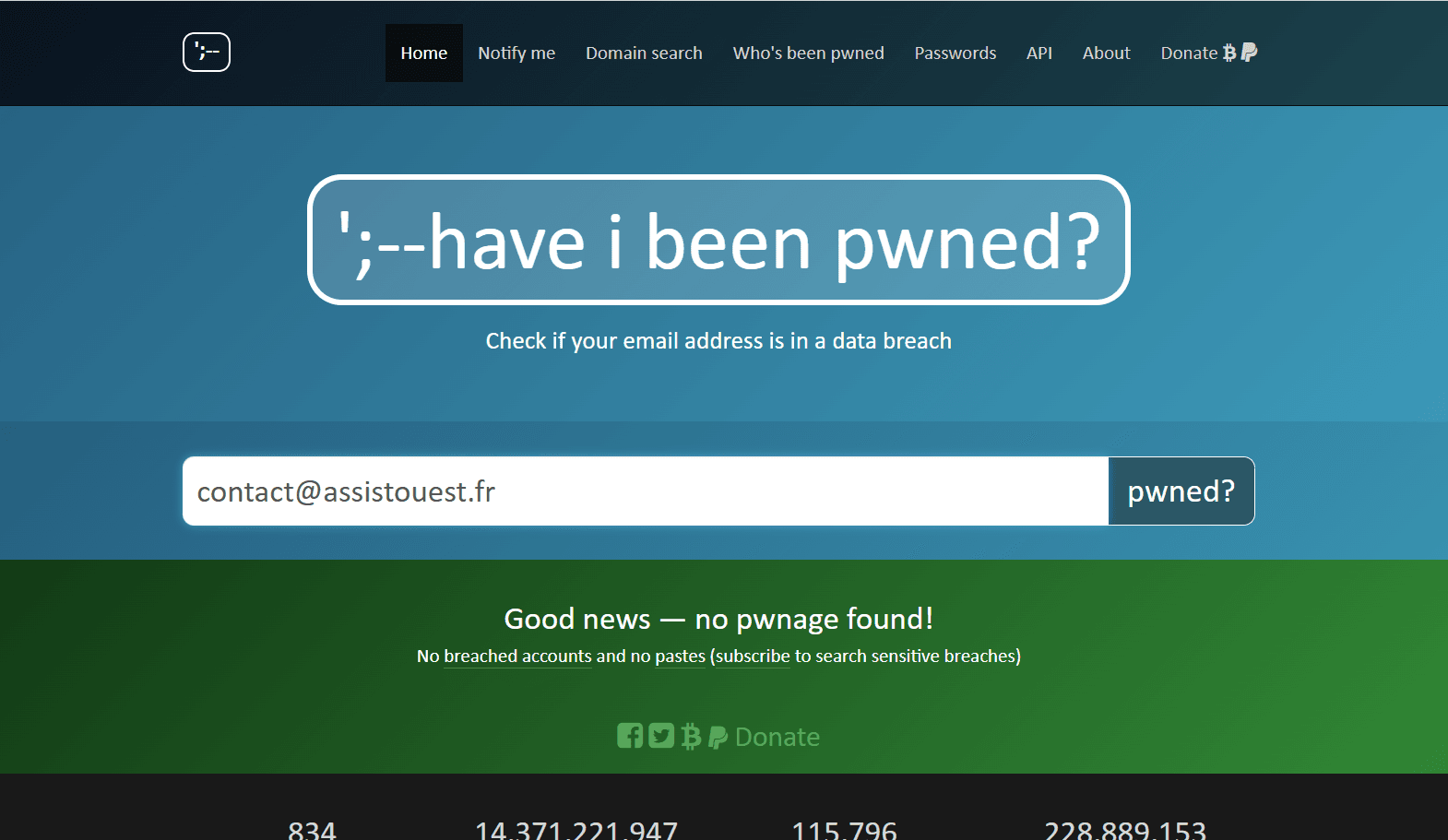
This free site lets you check whether your e-mail addresses or passwords are in databases stolen during cyber attacks. It’s easy: just enter your address, and in a matter of seconds you’ll know whether your information has been compromised. The site even features an automatic alert, warning you if your data is ever exposed.
Report on Google’s dark web
Google, always on the cutting edge, now offers a powerful tool for monitoring your data on the dark web: the Dark Web Report.
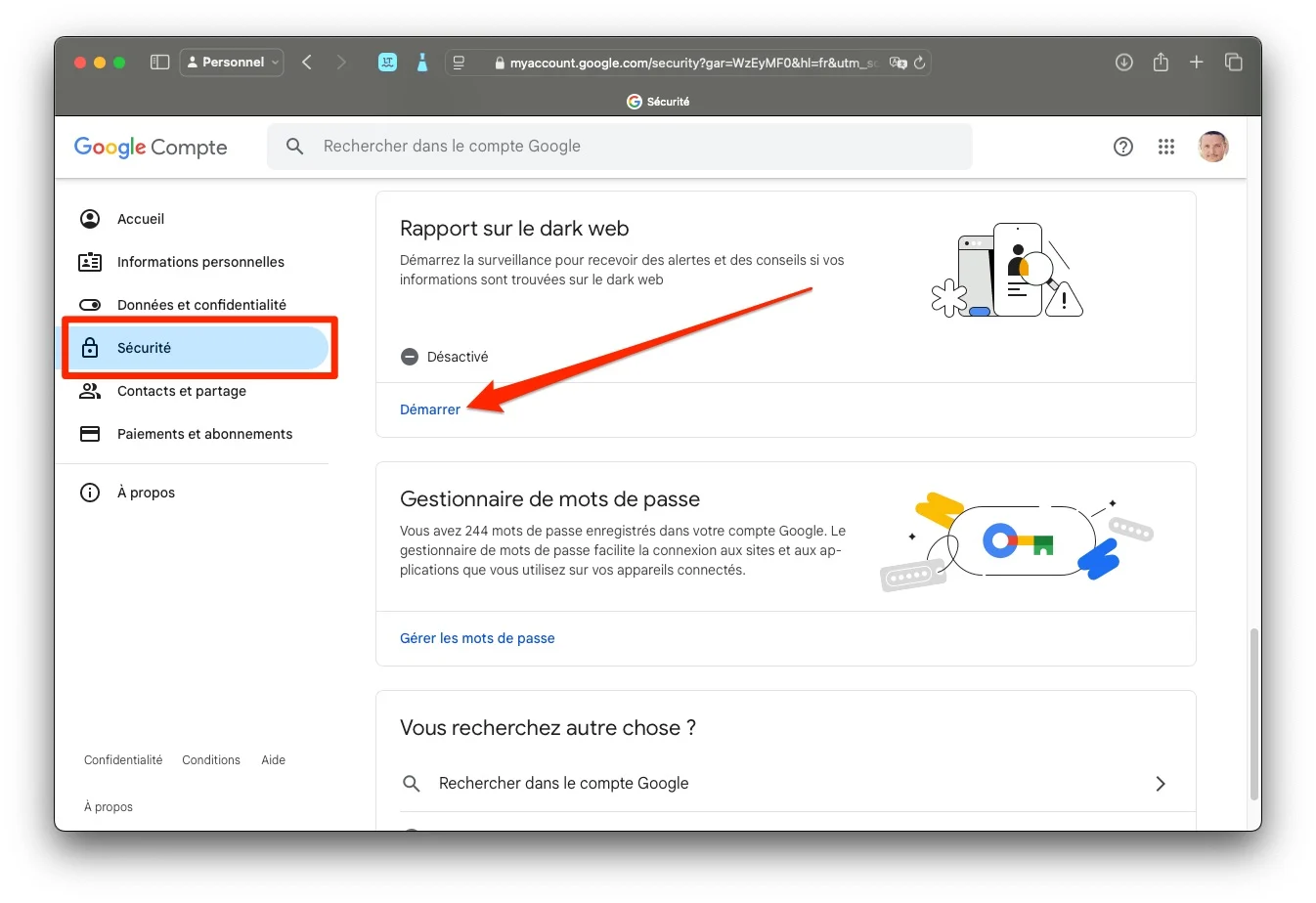
Free for all users with a Google account, this tool scans dark web platforms for information such as your name, e-mail address or phone number. Activation is simple: go to the security settings of your Google account and start monitoring. You’ll be alerted if any data linked to your profile is detected.
Antivirus protection for digital identity
Modern antivirus software is no longer limited to blocking viruses and malware. Today, many incorporate advanced monitoring tools, particularly to protect your digital identity against the risks of the dark web.
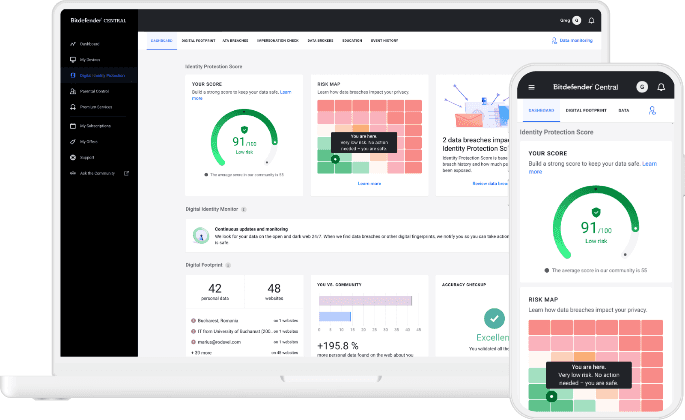
These features scan clandestine platforms where personal information such as e-mails, passwords or credit card numbers could be exchanged. In the event of detection, an alert is sent to you so you can act quickly: change your login details, activate two-factor authentication or contact the relevant departments.
Where do we draw the line between privacy and personal data?
Millions of companies collect, analyze and exploit information about us, often under the pretext of improving their services or personalizing our experiences. But at what cost?
Privacy is the fundamental right to control what we choose to show or keep to ourselves. Personal data, on the other hand, are the pieces of our digital identity: name, address, online behavior, location, preferences… And this is precisely where the problem lies. What used to be private – our habits, our opinions, our interactions – is now transformed into currency for the digital economy.
Two-speed ethics
Privacy policies, which are often long and incomprehensible, are also a problem. Who really reads them? Consent then becomes a simulacrum. We accept without really understanding what we’re sacrificing. Can we speak of a free choice when refusing the conditions means cutting ourselves off from essential services?
While some companies advocate transparency, they remain in the minority. Most adopt a purely economic logic: maximize profits at the expense of fundamental rights. Scandals like Cambridge Analytica or massive data breaches are just the tip of an iceberg.
Companies like Facebook, Google and Amazon claim to respect our personal data, while at the same time making it their core business. This paradox raises an essential question: can we really talk about privacy when every click, every movement is monitored, analyzed and monetized? Worse still, these companies themselves dictate the rules of the game.
Their interpretation of what is “ethical” is often far removed from the concerns of individuals.








Be the first to start the discussion!