You’re preparing to resell a computer or USB stick, and you want to be sure that no one can retrieve your files. A quick format is not enough, as the data is still present on the medium, invisible but still accessible. Under Windows, there are simple, free methods for permanently erasing a disk and preventing any recovery. Find out how to reset your media, prevent data recovery and give it away with confidence.
Permanently erase a Windows hard drive or USB key before resale
- Why completely erase a disc before resale?
- 1. Permanently erase a mechanical disk with the free Eraser software
- 2. Complete erasure of an SSD requires proprietary software
- Check that data has been erased
- The different methods of data destruction
- Controlling the total deletion of data
This article is based on international secure erasure standards (DoD 5220.22-M, NIST 800-88, ATA Secure Erase). It explains in a reproducible way how to permanently erase a hard disk, USB stick, SD card or SSD, based on the principles of storage physics and forensic analysis practices.
Why completely erase a disc before resale?
Before disposing of a computer, external hard drive or USB stick, it’s essential to ensure that all personal data has actually been deleted. A quick format or reset is not enough: these operations only delete references to files, without touching their content. The data remains on the disk, invisible to the average user, but easily recoverable with professional data recovery software.
Conventional formatting simply resets the file system allocation table (FAT, NTFS, exFAT). This is like removing the contents of a book without destroying the pages. Files can therefore be restored as long as they have not been rewritten with new data.
| Method | Principle | Average time | Safety | Recoverable data |
|---|---|---|---|---|
| Fast formatting | Deletes file index only | 1 to 2 minutes | Low | Easily with recovery software |
| Secure deletion | Multiple rewriting of random data | 30 min to several days | High | Irreversible |
| Destruction | Magnetic field removal or destruction | Instantaneous | High | Support unusable |
Secure erasure makes it impossible to reconstitute the original files, and even a thorough analysis cannot recover any data after complete secure erasure. This is the preferred method in sensitive sectors (defense, cybersecurity, companies handling confidential information) and the most reliable way of protecting your data before recycling a storage medium.
If you regularly handle hard disks to be erased (recovery, maintenance or resale), the easiest way is to use a single-bay hardware eraser. This device connects directly to the SATA disk and executes secure erasing protocols without going through Windows.
1. Permanently erase a mechanical disk with the free Eraser software
To securely and irreversibly delete all data from a hard disk or USB stick, Eraser is one of the best free tools available for Windows. This open source software replaces all existing data with random sequences and prevents any recovery using forensic analysis software.
- Start by downloading the latest version of the software from the official Eraser website.
- Once the download is complete, double-click on the installation file to launch the program.
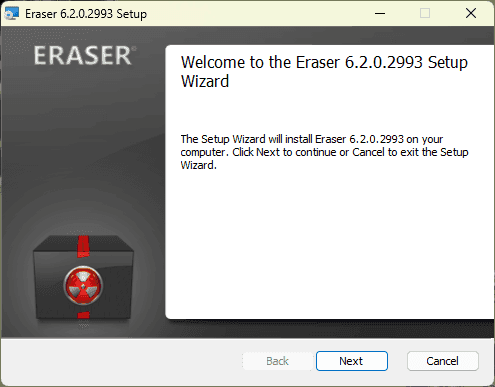
- Accept the terms of use, then choose Complete Installation. This option installs all the components required to run the software.
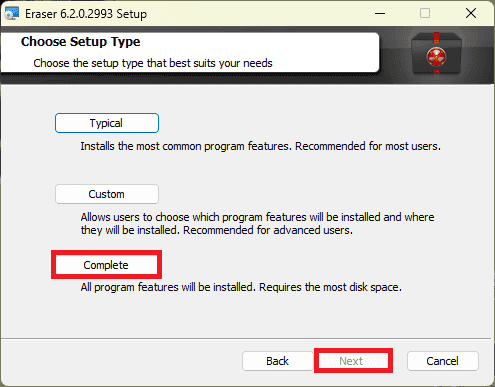
- Click Install and let the process run to completion. Depending on your computer’s performance, installation should take between one and two minutes.
When all is said and done, an Eraser shortcut appears on the desktop and in the Start menu. The software is now ready to use.
Open Eraser to access its main interface. The software’s operation is based on a task system that allows you to schedule or immediately execute a complete erasure.
- In the Eraser window, right-click and select New Task.
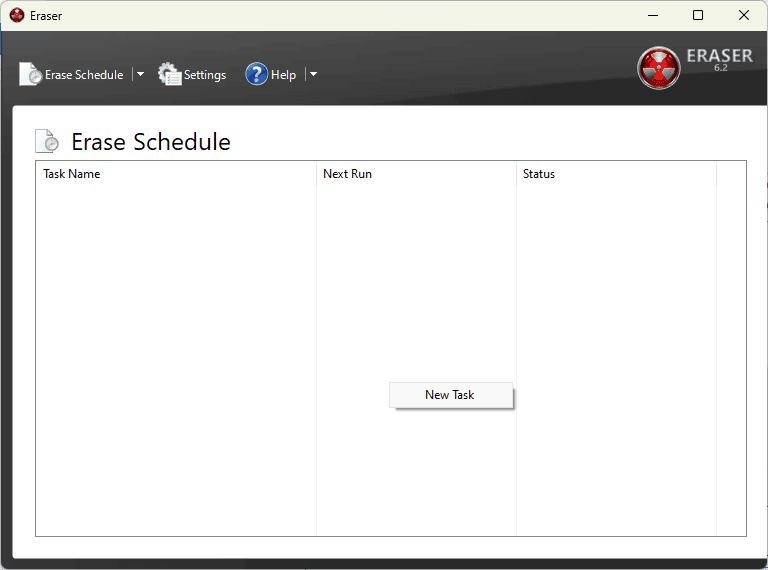
- Click on Add Data to indicate what you wish to delete.
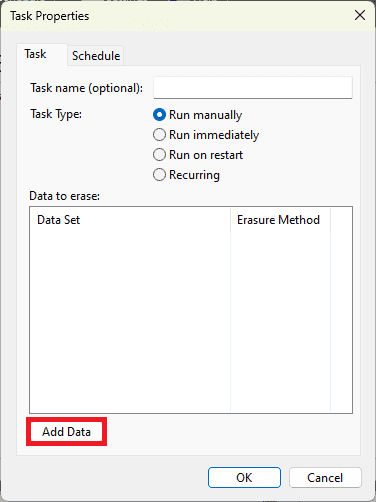
- In the window that opens, go to Target Type and choose Drive / Partition. This option lets you target an entire disk or a complete USB key.
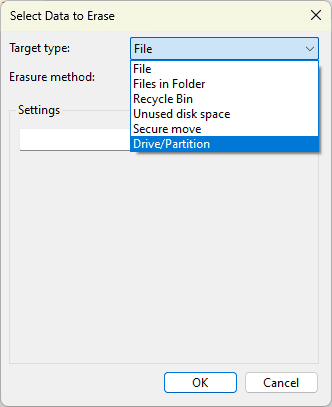
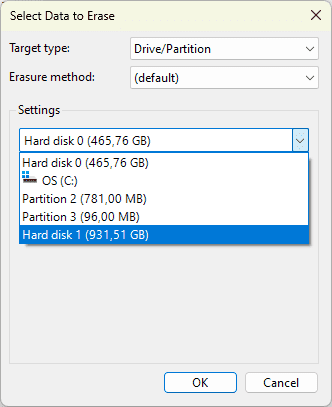
- Select the relevant drive from the list. Check carefully that you are not selecting your system disk (the C: drive), otherwise Windows will become unusable.
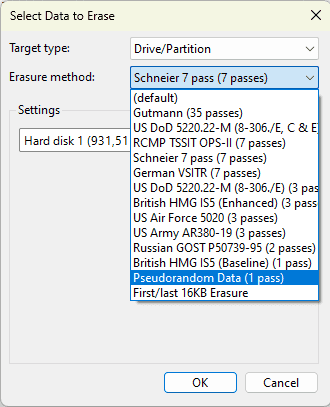
- In the Erasure Method list, select the erasure method:
- Pseudorandom Data (1 pass) rewrites the entire disk once with random data. This method is fast and sufficient for personal use.
- US DoD 5220.22-M (3 passes) performs three successive passes according to the US Department of Defense standard. It offers a more complete erasure, suitable for professional environments.
- Once the method has been selected, tick Run immediately, then click OK.
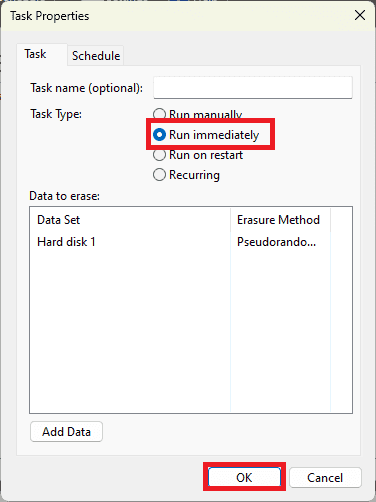
Eraser then starts the erasing process. The time required depends on the size of the disk and the number of passes selected.
- A 256 GB disk takes about 20 to 40 minutes with a single pass.
- A 1 TB disk with several passes can take several hours.
During the process, we recommend that you do not use the computer to avoid any interruption. The disk remains inaccessible until the operation has been completed.
2. Complete erasure of an SSD requires proprietary software
SSD disks use a completely different storage system to conventional hard disks. Instead of writing data to magnetic platters, they distribute it across electronic cells to extend their life. This internal workings can prevent conventional erasure software from rewriting the same memory blocks. A deletion algorithm designed for a mechanical disk cannot therefore guarantee complete erasure on an SSD, and may leave exploitable traces, even if the majority of data is erased.
To erase an SSD correctly, you need to use the manufacturer’s proprietary software. Each brand offers an official utility capable of sending the Secure Erase command directly to the internal controller. This command resets all memory cells to their original state, irreversibly deleting data even in areas inaccessible to Windows.

Simply download the software supplied by the manufacturer of your SSD (Samsung Magician, Crucial Storage Executive, Kingston SSD Manager or another brand). Once installed, the tool automatically recognizes the drive and offers a secure erase option. The program then prepares an internal operation that takes just a few minutes. At the end of the process, the SSD is completely empty, ready for reuse or reinstallation without any risk of recovery.
Check that data has been erased
After secure deletion, it’s important to check that the disk no longer contains any usable data. This step confirms that the procedure has been carried out correctly and that no traces have been left accessible using advanced analysis tools. You can use one of these free data analysis tools.
Analysis by these tools should confirm that the old files have been completely overwritten. If recovery software detects nothing, or if the hexadecimal blocks contain only random values, this means that the deletion is complete.
The different methods of data destruction
When it comes to eliminating information irreversibly, there are two distinct but complementary approaches. The first is to erase data using software processes that rewrite the information until it becomes unreadable. The second is based on the physical destruction of the medium, i.e. mechanical or electromagnetic action that prevents any possible recovery.
Both methods are designed to ensure that no data can be restored, even by the advanced analysis tools used in cybersecurity and digital forensics. Software erasure is the most practical solution for the general public, while hardware destruction is appreciated by companies, administrations and laboratories handling highly confidential data.
Physical methods of data destruction
When a disc contains sensitive information or can no longer be reused, physical destruction becomes the most radical solution. The aim of these methods is to render the medium irretrievably unusable.
They are often used by companies and public authorities. Before being destroyed, the disks are generally emptied by a complete software erasure to eliminate any residual traces. This double treatment combines logical security and hardware deletion.
| Method | Support concerned | Principle | Result |
|---|---|---|---|
| Degaussing | Magnetic hard disks (HDD) | Suppression of internal magnetic field | Data irretrievable, disk unusable |
| Physical destruction | HDD / SSD / USB | Drilling, cutting, mechanical crushing | Data destroyed, media unrecoverable |
| Furnace | HDD / SSD | Heating of NAND platters or chips beyond their melting point | Total destruction of components |
| Chemical spraying | Electronic disks or chips | Use of acids or solvents to dissolve circuits | Used in military applications |
| Disassembly and destruction of memory chips | SSD / USB memory stick | Physical extraction of NAND modules and targeted destruction | Irreversible destruction of memory cells |
Degaussing is a particularly effective technique for mechanical hard disks. It involves exposing the platters to an electromagnetic field strong enough to completely disorganize the magnetic particles responsible for data storage. Once demagnetized, the disk can no longer be read or rebuilt. This method has no effect on electronic media such as SSDs.
For the latter, destruction by drilling, crushing or thermal fusion physically eliminates the NAND chips that store the information. These processes are irreversible, making it absolutely impossible to recover any data, even in a specialized analysis laboratory.
Software-based secure deletion methods
Software erasure is based on the principle of completely rewriting the medium. Each sector of the disk is overwritten with new data, random or structured, until no usable trace remains. Unlike simple formatting, this operation affects the entire disk, not just the indexing table.
This method makes it possible to permanently erase information without damaging the media. Tools such as Eraser, DBAN or Blancco use different writing protocols recognized by standards organizations and cybersecurity services. Users can adapt the level of erasure to the sensitivity of the data to be deleted.
| Method | Number of passes | Security level | Description |
|---|---|---|---|
| Pseudorandom Data | 1 | High | Fast random rewriting for the general public |
| US DoD 5220.22-M (E) | 3 | Very high | Classic US military method |
| US DoD 5220.22-M (ECE) | 7 | Very high | Extended variant with additional passes |
| Gutmann | 35 | Extreme | Uses 35 different writing patterns, very long |
| Schneier 7-Pass | 7 | High | Developed by Bruce Schneier, efficient and renowned |
| Only First & Last 2KB | 1 | Low | Deletes only the first and last zones of each file |
| Random Zero / One Fill | 1 | Medium | Fills the disk with random zeros or ones |
Modern disks require fewer passes than in the past. A single random write is often enough to erase the entire content, but multi-pass methods are still used for environments where security takes precedence over runtime.
Controlling the total deletion of data
Erasing a medium is not a matter of emptying it, but of erasing its memory. Each method produces a different result, from quick formatting that simply masks the files to complete rewriting that dissolves all usable traces. On a mechanical hard disk, rewriting is enough to render the data inaccessible. On an SSD, on the other hand, only the Secure Erase command is capable of resetting every cell to zero.
The borderline between erasure and illusion lies in the choice of tool and knowledge of the process. Software like Eraser does the job for regular or domestic use. Sensitive environments rely on certified algorithms, capable of applying multiple writing schemes according to proven standards. And when the data exceeds the value of the hardware, physical destruction becomes a matter of course, not out of excess, but out of necessity.
Deleting a disk means regaining control over what you leave behind. It’s as much a question of technical rigor as it is of a culture of confidentiality. Choosing the right method means ensuring continuity between security, respect for data and confidence in the tools you use.